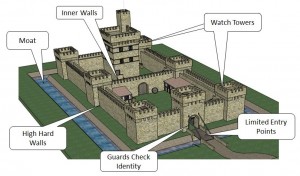
I was surprised to discover proof that my business is a target of cyber-criminals. After installing some security and reporting tools on my websites, I was alerted to the almost constant state of attack that they were under. And all I am doing is writing a cybersecurity blog. And you, dear reader, what of your business? There is a good chance that you are too, but simply don’t know it because ...
I was surprised to discover proof that my business is a target of cyber-criminals. After installing some security and reporting tools on my websites, I was alerted to the almost constant state of attack that they were under. And all I am doing is writing a cybersecurity blog. And you, dear reader, what of your business? There is a good chance that you are too, but simply don’t know it because ...
DEC