Continuing with my interview with Carolyn Heinze:
CH- What are the key ingredients of a sound security preparedness strategy?
- BW- They are:
- Patch
- Backup
- Keep anti-malware software updated
- Watch for and report suspected email exploits
- Good password policy coupled with two-factor authentication when possible
- Create an environment of cybersecurity awareness through training and fun employee events.
CH- When we think of cyber security, the tendency is to consider breaches that come from the outside. What can organizations do to protect themselves from breaches that can potentially come from the ...
Continue Reading →JAN

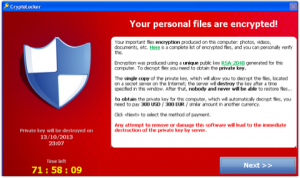 This is hot off the press. Yesterday
This is hot off the press. Yesterday  Another story from my friends at
Another story from my friends at  A virtual private network, or VPN, is a type of network computer connection that creates a private encrypted communications channel, commonly called a “tunnel,” when using insecure networks, such as in hotels and coffee shops, or when communicating over the Internet. Many businesses provide a VPN connection for their mobile and traveling employees. This means that when out of the office, a worker can open the VPN and be connected to ...
A virtual private network, or VPN, is a type of network computer connection that creates a private encrypted communications channel, commonly called a “tunnel,” when using insecure networks, such as in hotels and coffee shops, or when communicating over the Internet. Many businesses provide a VPN connection for their mobile and traveling employees. This means that when out of the office, a worker can open the VPN and be connected to ... There are many online accounts that would be bad to lose control of, such as your Amazon, eBay, PayPal, or bank account. But by the far the worst account to lose is your email account. If I can trick you into giving me your email user ID and password, by using a phishing email, or phone pretext call, I will be in. I can start off by simply observing, as I read your ...
There are many online accounts that would be bad to lose control of, such as your Amazon, eBay, PayPal, or bank account. But by the far the worst account to lose is your email account. If I can trick you into giving me your email user ID and password, by using a phishing email, or phone pretext call, I will be in. I can start off by simply observing, as I read your ... This post is a shout out to my peers in the cybersecurity profession, and especially those who would like to join us. I found these sites in two separate posts on
This post is a shout out to my peers in the cybersecurity profession, and especially those who would like to join us. I found these sites in two separate posts on  Quick answer: Yes it can! A
Quick answer: Yes it can! A