 This should really be called “anti-social” engineering. A good definition is “social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter.”
This should really be called “anti-social” engineering. A good definition is “social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter.”
My article on Wednesday will give an example of phone based social engineering – the fake tech support call. ...
Continue Reading →FEB

 There is a small company in the Czech Republic called
There is a small company in the Czech Republic called  Monday we looked at issues with the business class routers at Juniper Networks and Cisco Systems. Today we are going to look at an exploit affecting the Ubiquiti brand of cable modems.
Monday we looked at issues with the business class routers at Juniper Networks and Cisco Systems. Today we are going to look at an exploit affecting the Ubiquiti brand of cable modems. At the end of December last year Juniper Networks discovered that some malicious actors had added code to the firmware and software that run their routers, creating a back door that would allow attackers to access the router remotely, assume administrator privileges, and view and decrypt VPN traffic running through the routers. As the story unfolded, it turns out that Juniper was using a random number generator from NIST, and that the ...
At the end of December last year Juniper Networks discovered that some malicious actors had added code to the firmware and software that run their routers, creating a back door that would allow attackers to access the router remotely, assume administrator privileges, and view and decrypt VPN traffic running through the routers. As the story unfolded, it turns out that Juniper was using a random number generator from NIST, and that the ...


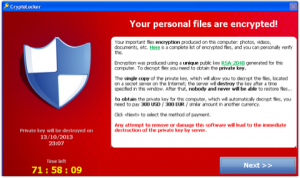 This is hot off the press. Yesterday
This is hot off the press. Yesterday