 Keeping our connected devices secure has become easier – and harder! Easier because we have more tools to defend our online assets, and harder because the opposition has grown much larger and become more sophisticated. And the enemy is not limited to criminals, there are terrorist groups, nation-state sponsored cyber operations teams, hacktivists, and other with malicious intent and nefarious schemes.
Keeping our connected devices secure has become easier – and harder! Easier because we have more tools to defend our online assets, and harder because the opposition has grown much larger and become more sophisticated. And the enemy is not limited to criminals, there are terrorist groups, nation-state sponsored cyber operations teams, hacktivists, and other with malicious intent and nefarious schemes.
When I started writing this blog in October 2006, almost 2000 ...
Continue Reading →OCT


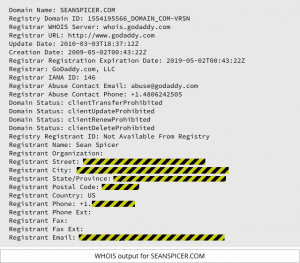 I will start out by admitting that I hate Domain Privacy. But I just read a story in
I will start out by admitting that I hate Domain Privacy. But I just read a story in  In the last several days, we have seen big distributed denial of service (DDoS) attacks against DynDNS, an Internet services company that provides domain name services (DNS) to many companies including Twitter and PayPal. DNS is how web sites are found on the web, you enter a web address in your browser, and DNS finds the website you are looking for. When attacked in ...
In the last several days, we have seen big distributed denial of service (DDoS) attacks against DynDNS, an Internet services company that provides domain name services (DNS) to many companies including Twitter and PayPal. DNS is how web sites are found on the web, you enter a web address in your browser, and DNS finds the website you are looking for. When attacked in ... When I am doing a cybersecurity presentation, someone is bound to ask about the Dark Web. What is it, exactly, and how does someone get there? The how part we discussed on Friday.
When I am doing a cybersecurity presentation, someone is bound to ask about the Dark Web. What is it, exactly, and how does someone get there? The how part we discussed on Friday.  You don’t need to be a journalist, freedom fighter, or living under an oppressive political regime to have the desire for some online privacy. Maybe you are trying to put the contents of your life back into the Pandora’s box you opened when you signed up on Facebook. Maybe you would like a little privacy in your online life.
You don’t need to be a journalist, freedom fighter, or living under an oppressive political regime to have the desire for some online privacy. Maybe you are trying to put the contents of your life back into the Pandora’s box you opened when you signed up on Facebook. Maybe you would like a little privacy in your online life. I discovered a while ago that my LG smart phone can be used fairly easily to make a surreptitious video of a meeting simply by turning on the video camera and slipping the phone into a shirt pocket. The camera lens clears the edge of the pocket nicely, and there is no indication, at least on my phone, the the camera is rolling. This is a great way to keep a record ...
I discovered a while ago that my LG smart phone can be used fairly easily to make a surreptitious video of a meeting simply by turning on the video camera and slipping the phone into a shirt pocket. The camera lens clears the edge of the pocket nicely, and there is no indication, at least on my phone, the the camera is rolling. This is a great way to keep a record ... You took the red pill, and now you want to see how deep the rabbit hole goes. You spend a lot of time on computers, and use them for things that your friends think are odd. You are on your third Raspberry Pi project. You are running Linux on at least one computer. Now you want to learn the light and dark arts ...
You took the red pill, and now you want to see how deep the rabbit hole goes. You spend a lot of time on computers, and use them for things that your friends think are odd. You are on your third Raspberry Pi project. You are running Linux on at least one computer. Now you want to learn the light and dark arts ...
