Catch of the Day: IONOS Blocked Message Phish
Examples of clever phish that made it past my anti-spam nets and into my inbox. Some are contributed by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
IONOS Blocked Message Phish
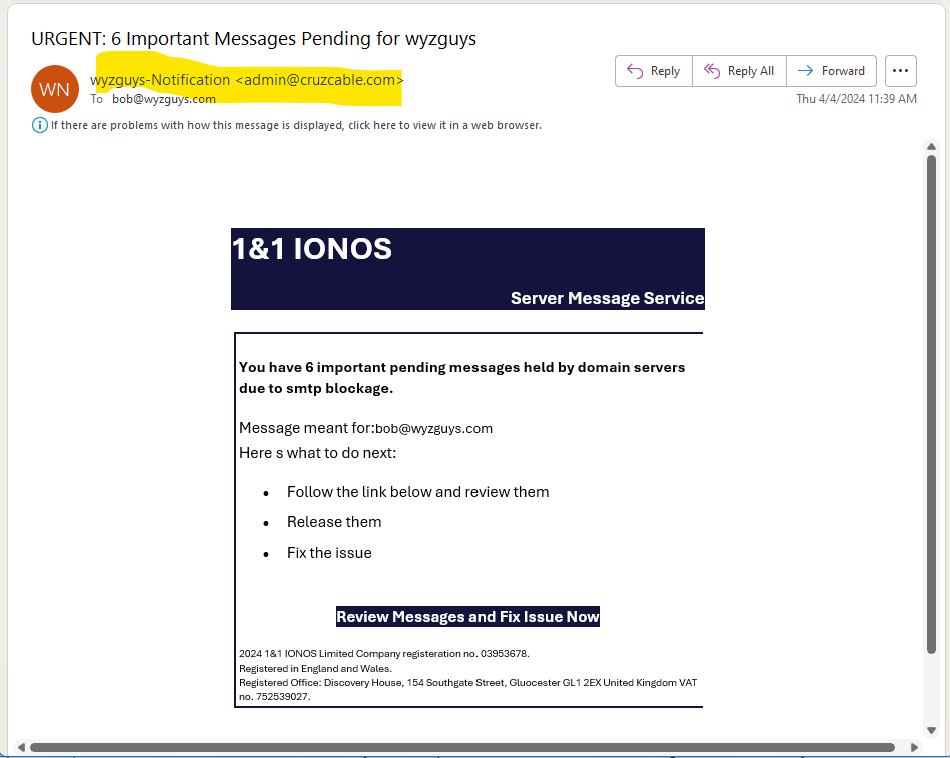
Here’s another phishing email that looks like it is from my email host. The sender address is from admin@cruzcable.com, which is wrong from the IONOS domain. The Review Messages and Fix Issue Now button resolves to https://phaseonelandscepes.com/index.html, which is also a suspicious domain. And landscepes is misspelled. So many problems!
Here’s a look at the original email. It arrived at 11:30 AM on Thursday 2024-04-04. When I dug into this 4 hours later it had still not been flagged by Virustotal.
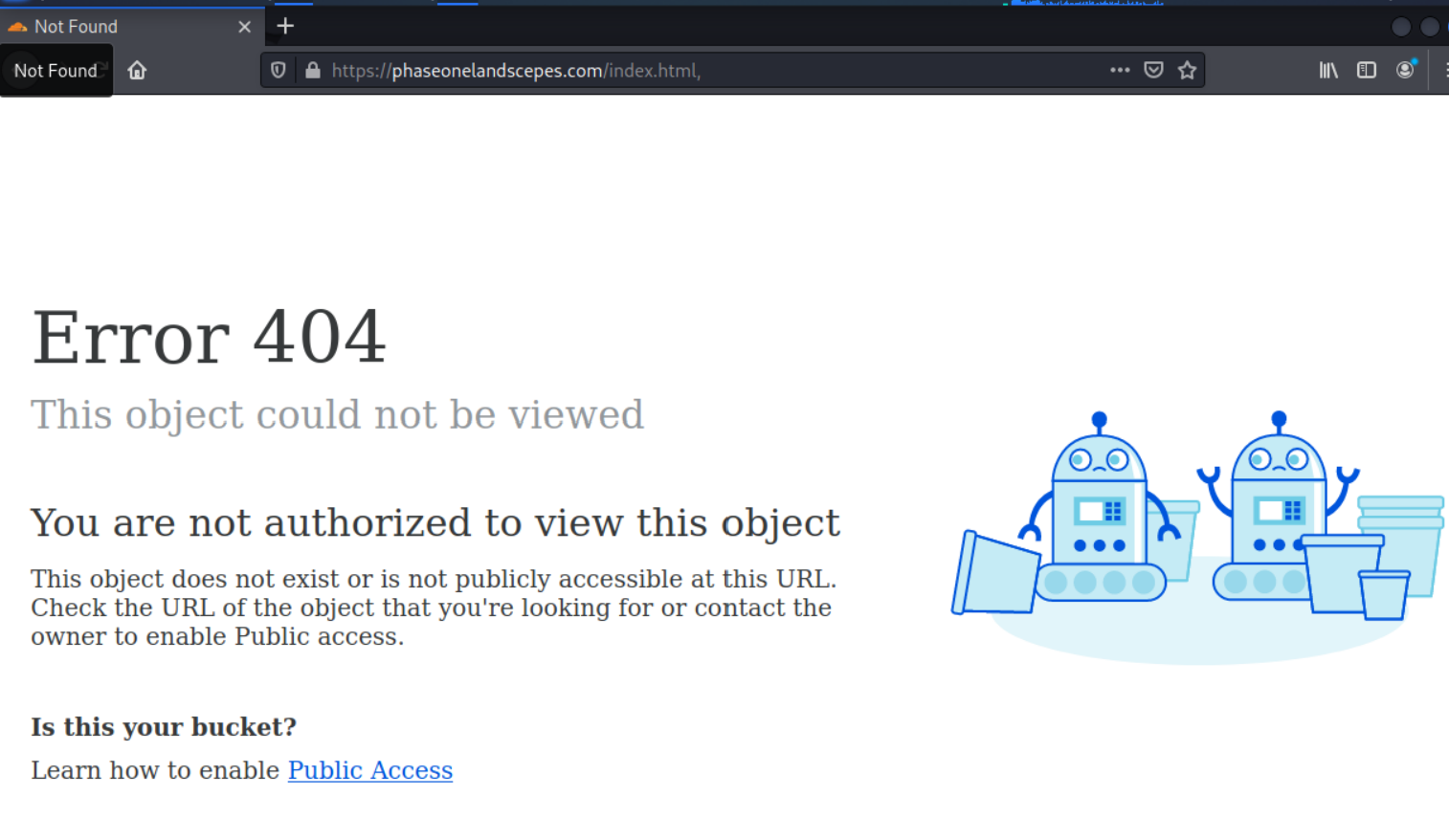
I opened up Kali Linux and took a look at the landing pages, which started off with a CAPTCHA that required me to identify the motorcycles in two sets of images. A very nice touch, and they worked!. The next landing page was a 404 Not Found, so something is broken, or possibly this exploit has been taken down, or maybe was never completely built-out?
Here is the 404 page. I did a quick search on the line “Is this your bucket?” and found this error message and 404 page belongs to Joe Sandbox http://joesandbox.com.
Joe Sandbox appears to be an alternative to Virustotal, my favorite analysis site. I decided to register for this service and give it a test drive.
Here is the Virustotal results, and I am honestly surprised that this URL had not been flagged yet.
Hard to know what the attacker was going for. Perhaps this was just a trial run. Maybe the exploit was executed improperly. A lot of that going around in the Exploit as a Service marketplace.
Share
APR








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com