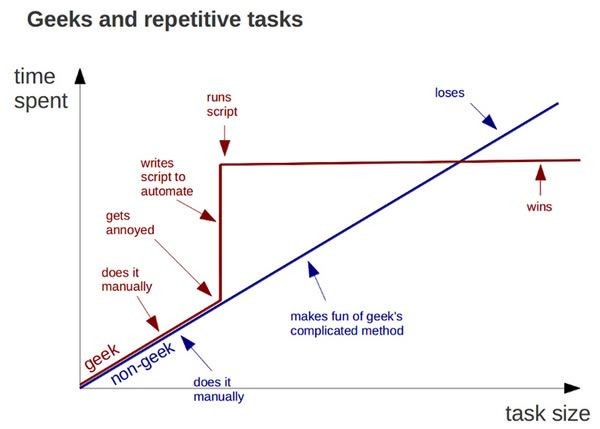
I know I usually focus on writing articles that are useful to the average business owner or computer user, but I received something in my inbox recently that I just have to share. This is from another blog on Postmodern Security titled “MALWARE ANALYSIS AND INCIDENT RESPONSE TOOLS FOR THE FRUGAL AND LAZY”. If you are a cybersecurity professional you ...
I know I usually focus on writing articles that are useful to the average business owner or computer user, but I received something in my inbox recently that I just have to share. This is from another blog on Postmodern Security titled “MALWARE ANALYSIS AND INCIDENT RESPONSE TOOLS FOR THE FRUGAL AND LAZY”. If you are a cybersecurity professional you ...
OCT