 Classical computer and network security has relied on perimeter defense, in the form of firewalls, intrusion detection devices, and similar technologies for quite some time. This is usually coupled with some form of endpoint security, typically in the form of a security software package. We are finding that this no longer is working. The reasons are many, but the big one is that there is no perimeter anymore.
Classical computer and network security has relied on perimeter defense, in the form of firewalls, intrusion detection devices, and similar technologies for quite some time. This is usually coupled with some form of endpoint security, typically in the form of a security software package. We are finding that this no longer is working. The reasons are many, but the big one is that there is no perimeter anymore.
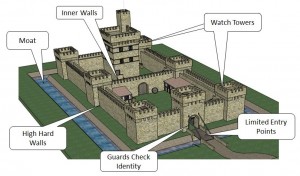
Perimeter defenses work like medieval castle defenses, and work best when there are no assets outside the walls to defend. This, of course, is no longer the case. Just as medieval towns grew outside the battlements, our networks have expanded to include things like branch offices and remote workers connected via the Internet, vendor and other third party connections to our networks, and a plethora of cloud-based services starting with email, and moving on to file storage, web applications, web sites, and hosted servers including domain controllers, and even entire data centers.
In order to adequately defend this far flung and diverse network, you need to answer a lot of questions.
- What and where are all of your assets?
- What does your user group do, what do they need to access?
- What does your network traffic look like?
Defense these days means knowing what is happening inside the network, what is normal, what is necessary, what is critical, and what is wrong. It means actively monitoring with some form of intelligence. It means going deeper than you ever have before, and really understanding what is happening.
Pete Herzog wrote an excellent spoof of the typical “3 steps to perfection” sort of articles you see all the time. Step three is a doozy, but much closer to reality than the first two steps. I have included a link to it below.
More information :
ShareDEC




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com