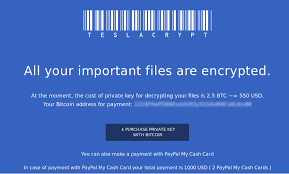
 Crypto-ransomware continues to be one of the most popular money making exploits for cyber criminals. The reason for this is simple; its works, and the return on investment is quite high. According to a recent article in Naked Security, the score will reach $1 billion in 2017.
Crypto-ransomware continues to be one of the most popular money making exploits for cyber criminals. The reason for this is simple; its works, and the return on investment is quite high. According to a recent article in Naked Security, the score will reach $1 billion in 2017.
A poll by the IBM company found that nearly 50% of the businesses polled had been hit by ransomware, and of those 70% paid ...
Continue Reading →JAN

 The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC.
The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC. As we approach year-end, many small and medium sized business owners and managers are coming to the realization that their best intentions for creating a cybersecurity program in their organization have fallen short. This was the year, you promised yourself, that we get a handle on computer and network security.
As we approach year-end, many small and medium sized business owners and managers are coming to the realization that their best intentions for creating a cybersecurity program in their organization have fallen short. This was the year, you promised yourself, that we get a handle on computer and network security. Naked Security
Naked Security On Monday we looked at the some of the primary attack vectors used by cyber-criminals. Here are the rest of the attack vectors that Kevin Thompson from FireEye shared at the Cyber Security Summit. Many of these are significant twists on old exploits, or more sophisticated exploits.
On Monday we looked at the some of the primary attack vectors used by cyber-criminals. Here are the rest of the attack vectors that Kevin Thompson from FireEye shared at the Cyber Security Summit. Many of these are significant twists on old exploits, or more sophisticated exploits. We have written about Stuxnet a couple of times. (
We have written about Stuxnet a couple of times. ( We have been recommending Windows Defender as an acceptable anti-malware program. What we like about it is that it comes baked into the Windows 10 operating system, and gets its malware definitions updates with the other Windows security and feature updates that users are already receiving. And it is free. Plus it keeps your system a little less cluttered than adding a third party anti-malware product.
We have been recommending Windows Defender as an acceptable anti-malware program. What we like about it is that it comes baked into the Windows 10 operating system, and gets its malware definitions updates with the other Windows security and feature updates that users are already receiving. And it is free. Plus it keeps your system a little less cluttered than adding a third party anti-malware product.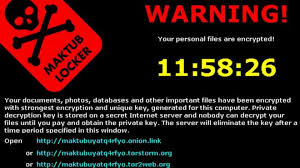 Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at ...
Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at ... Having just discussed phishing on Monday, it makes sense to cover the social engineering practice called “baiting” today. Typically, this involves an attacker leaving removable media such as a USB flash drive or SD Media card lying around in a public location. The exploit depends entirely on the principle of “finders-keepers.” People pick these drives up, and plug them into the first computer ...
Having just discussed phishing on Monday, it makes sense to cover the social engineering practice called “baiting” today. Typically, this involves an attacker leaving removable media such as a USB flash drive or SD Media card lying around in a public location. The exploit depends entirely on the principle of “finders-keepers.” People pick these drives up, and plug them into the first computer ...