Thanks to Bruce Schneier for linking this out in a recent email.
Continue Reading →AUG
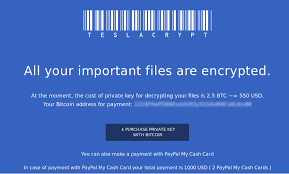 You have trained your staff and improved your defenses. In spite of your best efforts, you have an active case of crypto-malware running on a system in your business. How do you recover?
You have trained your staff and improved your defenses. In spite of your best efforts, you have an active case of crypto-malware running on a system in your business. How do you recover?
Here are the steps to recovery:
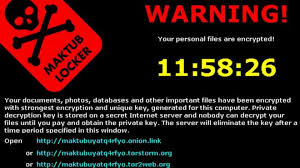 Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at ...
Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at ...
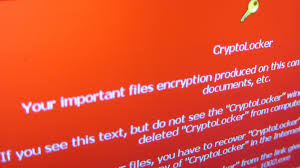 This week we will be focusing on preventing, detecting, and recovering from the many variants of the crypto-ransomware exploit. Ransomware attacks, such as CryptoLocker, CyrptoWall, Locky, Chimera, Zepto, and the like, have become one of the best money-making exploits for cyber-criminals, with new variants appearing on the scene every month. These attacks usually start with a phishing email and a ZIP file attachment or a malicious link, so email vigilance can ...
This week we will be focusing on preventing, detecting, and recovering from the many variants of the crypto-ransomware exploit. Ransomware attacks, such as CryptoLocker, CyrptoWall, Locky, Chimera, Zepto, and the like, have become one of the best money-making exploits for cyber-criminals, with new variants appearing on the scene every month. These attacks usually start with a phishing email and a ZIP file attachment or a malicious link, so email vigilance can ...
 I am a regular listener and fan of Joe Soucheray’s Garage Logic radio show. One of the persistent themes on the show is the “Samer Therory.” Joe explains:
I am a regular listener and fan of Joe Soucheray’s Garage Logic radio show. One of the persistent themes on the show is the “Samer Therory.” Joe explains:
“Samer, as it was explained to me, was a guy in the military back in the 1970s. He worked in the communications field. He posited then, and it seems to be ...
Continue Reading → I will be a featured presenter at the MN Blogger Conference, on Saturday October 15, at Concordia University in St.Paul, from 8:15 am to 5:15 pm. Tickets are $20.
I will be a featured presenter at the MN Blogger Conference, on Saturday October 15, at Concordia University in St.Paul, from 8:15 am to 5:15 pm. Tickets are $20.
My presentation is titled Shields Up For WordPress Websites and Blogs.
In this presentation you will learn why WordPress sites are an attractive target for cyber-criminals and attackers, why they want to hijack your site, and ...
Continue Reading → Actually there are way more than ten ways, but here are some I see all the time. We can play this like a game, so go ahead and give yourself a point for each one of these that apply to you. This game scores like golf – low score wins.
Actually there are way more than ten ways, but here are some I see all the time. We can play this like a game, so go ahead and give yourself a point for each one of these that apply to you. This game scores like golf – low score wins.
 Should you hire a hacker? Recently, the US Department of Defense did just that in their “Hack the Pentagon” event this spring. This event resulted in the discovery of over 200 vulnerabilities that have been remediated, making our Defense network more secure.
Should you hire a hacker? Recently, the US Department of Defense did just that in their “Hack the Pentagon” event this spring. This event resulted in the discovery of over 200 vulnerabilities that have been remediated, making our Defense network more secure.
The hackers we are recommending would be Certified Ethical Hackers (CEH) or Offensive Security Certified Professionals (OSCP). These are professional cybersecurity practitioners who have received the specialized training ...
Continue Reading →Another election year. Use your vote carefully. Vote early, vote often. Remember, a vote for a third party candidate is just like “none of the above.”
Thanks to my Uncle Ron, I have an example of politics in action for your amusement.
So I told my son “I want you to marry a girl of my choice!”
He said “NO!”
I told him its Bill Gates daughter!!!!
He said “OKAY!”
Got in contact with Bill Gates & told him “I want your daughter to marry my son!”
He said “NO!”
I Told him ...
Continue Reading → Many small businesses are being dragged into the arena of IT risk assessment by larger client companies, suppliers, or regulators. Common scenarios include credit card (PCI) or HIPAA compliance. Since the Target breach, smaller vendors and supplier companies who have a network connection into the IT operations of a larger company are being required to undergo the same sort of vulnerability and risk assessment ...
Many small businesses are being dragged into the arena of IT risk assessment by larger client companies, suppliers, or regulators. Common scenarios include credit card (PCI) or HIPAA compliance. Since the Target breach, smaller vendors and supplier companies who have a network connection into the IT operations of a larger company are being required to undergo the same sort of vulnerability and risk assessment ...