 This is not a new story, and I decided not to write about it when this “sale” of pilfered NSA hacking tools was offered last August by a group identified as the Shadow Brokers. But this story has taken an amusing turn, so I have included it in a Tuesday post.
This is not a new story, and I decided not to write about it when this “sale” of pilfered NSA hacking tools was offered last August by a group identified as the Shadow Brokers. But this story has taken an amusing turn, so I have included it in a Tuesday post.
The stolen trove of NSA goodies was originally offered as a winner ...
Continue Reading →OCT

 When I am doing a cybersecurity presentation, someone is bound to ask about the Dark Web. What is it, exactly, and how does someone get there? The how part we discussed on Friday.
When I am doing a cybersecurity presentation, someone is bound to ask about the Dark Web. What is it, exactly, and how does someone get there? The how part we discussed on Friday.  When you lose your login credentials to an online account, it can be devastating. Depending on what was compromised and what was lost, you may have an expensive and time-consuming task on your hands. So the bad guys took your user ID and password, or some other personal information. Was it worth it? There is an active resale market for this information, and ...
When you lose your login credentials to an online account, it can be devastating. Depending on what was compromised and what was lost, you may have an expensive and time-consuming task on your hands. So the bad guys took your user ID and password, or some other personal information. Was it worth it? There is an active resale market for this information, and ... If I can get your user name and password, I can easily break into and use your computer and network resources just as if I were you. Bruce Schneier wrote an article recently that discussed this issue. Many of the largest exploits are started with
If I can get your user name and password, I can easily break into and use your computer and network resources just as if I were you. Bruce Schneier wrote an article recently that discussed this issue. Many of the largest exploits are started with 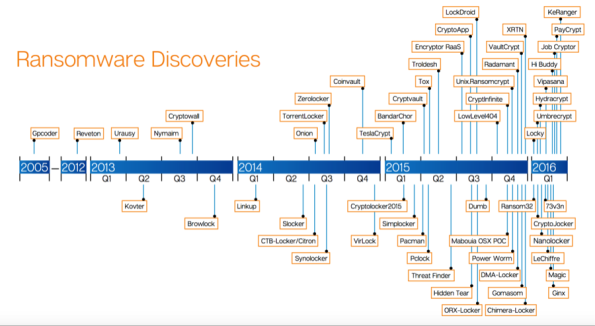
 One of the very worst breaches that can happen to you is for an attacker to be able to access your email account. If someone else can access your email, and read the messages you send and receive, and access your contact list and calendar, then they can learn many personal details about you that would make it easier to steal your identity, access other web accounts using the password reset ...
One of the very worst breaches that can happen to you is for an attacker to be able to access your email account. If someone else can access your email, and read the messages you send and receive, and access your contact list and calendar, then they can learn many personal details about you that would make it easier to steal your identity, access other web accounts using the password reset ... A recent rule by the Supreme Court has given the FBI authority to hack your computer if it is inadvertently part of a criminal botnet. Recent changes to a procedural rule known as
A recent rule by the Supreme Court has given the FBI authority to hack your computer if it is inadvertently part of a criminal botnet. Recent changes to a procedural rule known as  You took the red pill, and now you want to see how deep the rabbit hole goes. You spend a lot of time on computers, and use them for things that your friends think are odd. You are on your third Raspberry Pi project. You are running Linux on at least one computer. Now you want to learn the light and dark arts ...
You took the red pill, and now you want to see how deep the rabbit hole goes. You spend a lot of time on computers, and use them for things that your friends think are odd. You are on your third Raspberry Pi project. You are running Linux on at least one computer. Now you want to learn the light and dark arts ...