The cyber-criminal underground has found a real moneymaker in the various forms of encryption based ransomware schemes. These exploits turn all your readable work product, your documents, pictures, music and video files, into a collection of encrypted gibberish, and then kindly offers to sell you the decryption key. I recently saw an infographic from Symantec on the Bromium blog that illustrated the problem perfectly.
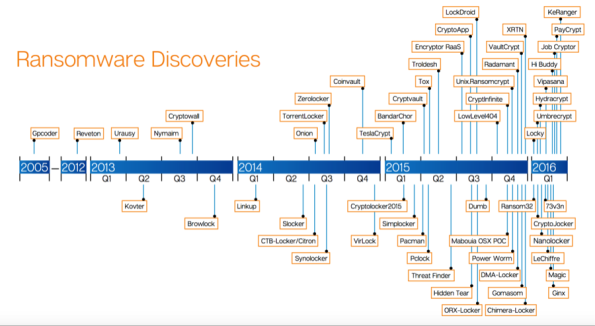
What we see is an early outlier in 2005 and then, starting in 2012, there is a steady increase in the number of crypto-ware exploits. Ransomware has increased 600 percent since 2013, and doubled last year in 2015. These exploits are becoming more targeted, more sophisticated, and tougher to detect in the earlier stages of an infection.
According to security intelligence firm LogRhythm, $209 million has been paid to ransomware criminals in the first quarter of 2016. The FBI estimates that business losses from ransomware will exceed $1 billion in 2016. The reason that Hollywood Presbyterian Medical Center paid $17,000 for the decryption key was that they were losing $100,000 per day just from the CT scanning department.
All of these exploits rely on social engineering or phishing attacks to get started, which means that your inbox is the source of these problems. We recommend the following practices to mitigate the risks associated with these threats and exploits.
- Never click on a link or open an attachment without confirming the destination of the link or contents of an attachment. The website VirusTotal.com can help you here. Too. hard to check? Don’t click! Ever!
- Make sure you have a working backup program, and verify that you can restore from the backups when it becomes necessary.
- You might give a look to the Anti-Ransomware Beta from Malwarebytes. This is not recommended for production networks yet, but you should be testing this one and giving it serious consideration.
- Sophos also has made improvements to their endpoint security product to focus on detecting ransomware code early and preventing it from running.
This particular exploit is tough to defend, and even harder to overcome once you have been infected. Your options are restore from backup, or pay the ransom, and both options are expensive. To prevent a network wide infection you need to identify infected systems and isolate them from the rest of your network. For a more complete solution set, check out this article on US-CERT. But keep in mind that prevention is your best option, once the data has been encrypted there is no cure but to pay for the decryption key.
More information:
- Malwarebytes Anti-Ransomware Beta
- Bromium article
- US-CERT Ransomware and Recent Variants
- LogRhythm infographic download
MAY




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com