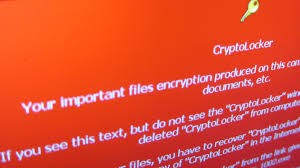
 According to a recent article on Naked Security, not at all hard. While at Black Hat in Las Vegas, researchers from Sophos gave a presentation that dissected the “Philadelphia” ransom software as a service (SaaS) model.
According to a recent article on Naked Security, not at all hard. While at Black Hat in Las Vegas, researchers from Sophos gave a presentation that dissected the “Philadelphia” ransom software as a service (SaaS) model.
Anyone can buy the Philadelphia ransomware kit on the Dark Web for $400. And for this nominal investment, the would-be attacker gets a simple executable file that sets up the whole system automatically. ...
Continue Reading →AUG


 Certain personal records are a gold mine for cyber-criminals and identity thieves. Highly targeted personal information include your medical records, tax information, social security number, driver’s license, and even odd bits such as utility bills, and retail or airline loyalty rewards points. Any of this information can be sold on the Dark Web, or used directly to get free ...
Certain personal records are a gold mine for cyber-criminals and identity thieves. Highly targeted personal information include your medical records, tax information, social security number, driver’s license, and even odd bits such as utility bills, and retail or airline loyalty rewards points. Any of this information can be sold on the Dark Web, or used directly to get free ... Passwords are not dead – not yet. But they are on life support. They are no longer enough to truly secure anything on their own.
Passwords are not dead – not yet. But they are on life support. They are no longer enough to truly secure anything on their own. On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims.
On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims. What is a web browser? Can you name the ones you use? Here’s a hint: it is the most frequently used computer application. A computer application is a software program the performs a certain function. When you “surf the web,” access the Internet, shop online, keep in touch with Facebook, and for many people, read and send email, you are using a ...
What is a web browser? Can you name the ones you use? Here’s a hint: it is the most frequently used computer application. A computer application is a software program the performs a certain function. When you “surf the web,” access the Internet, shop online, keep in touch with Facebook, and for many people, read and send email, you are using a ... The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC.
The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC. This actually is in the “good news” department. The some security folks at Facebook are scouring the Dark Web, looking for rainbow tables of user names and passwords in order to find Facebook users who may be reusing the same password on multiple sites. As we have discussed here many times, password reuse creates a serious security vulnerability. If the cyber-crooks have your password for one site, they will try it on ...
This actually is in the “good news” department. The some security folks at Facebook are scouring the Dark Web, looking for rainbow tables of user names and passwords in order to find Facebook users who may be reusing the same password on multiple sites. As we have discussed here many times, password reuse creates a serious security vulnerability. If the cyber-crooks have your password for one site, they will try it on ... The answer to this question is complicated, but not impossible to understand. The first thing to know is that most passwords are not cracked by guessing, or trying thousands of possibilities one at a time on a typical login screen. Most systems will lock the account after a certain small number of failed attempts, like 5 or 6. This makes the kind of ...
The answer to this question is complicated, but not impossible to understand. The first thing to know is that most passwords are not cracked by guessing, or trying thousands of possibilities one at a time on a typical login screen. Most systems will lock the account after a certain small number of failed attempts, like 5 or 6. This makes the kind of ...