It’s Halloween tomorrow, the traditional time when we dress up in scary or not-so scary costumes to disguise our identity and trick our friends and family. It’s good to remember that malware often uses disguises to trick us into committing an action that releases the attack. What follows are my scary Halloween stories.
It’s Halloween tomorrow, the traditional time when we dress up in scary or not-so scary costumes to disguise our identity and trick our friends and family. It’s good to remember that malware often uses disguises to trick us into committing an action that releases the attack. What follows are my scary Halloween stories.
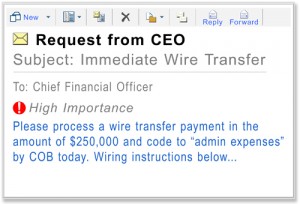
- Social Engineering – In this exploit the attacker may present themselves in person, over the phone, or by email, ...
OCT