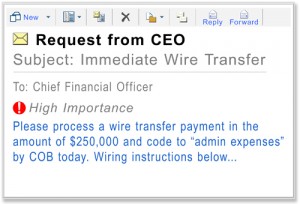
 Since 2013, cyber-criminal gangs working from the Middle East, Africa, and eastern Europe have scammed businesses out of $1.2 billion dollars worldwide, with over 700 US businesses reporting $747 million in losses to this exploit. In 2015 alone there has been a 270% increase in losses to this scam. On August 28th, the FBI warned business owners and manager to be on guard for what they are calling “Business Email Compromise” or BEC scams, which use spearphishing emails that appear to come from a regular supplier or vendor, or even the CEO of the target company.
Since 2013, cyber-criminal gangs working from the Middle East, Africa, and eastern Europe have scammed businesses out of $1.2 billion dollars worldwide, with over 700 US businesses reporting $747 million in losses to this exploit. In 2015 alone there has been a 270% increase in losses to this scam. On August 28th, the FBI warned business owners and manager to be on guard for what they are calling “Business Email Compromise” or BEC scams, which use spearphishing emails that appear to come from a regular supplier or vendor, or even the CEO of the target company.
These groups are targeting companies that have overseas branches, employees, or vendors, and who regularly send wire transfer payments. They are doing sophisticated research on their targets, by compromising their email accounts using stolen passwords or social engineering. They will read emails until they gather enough information about regular invoices and billing practices to sent a carefully designed email that looks like a legitimate email from a know supplier. The invoices are paid using electronic fund transfer to bank accounts in the control of the cyber-criminals, and usually located in places like China. Losses average about $130,0000, but in one notable case the loss was $737,000. Recovery of funds has been largely unsuccessful.
The FBI recommends that businesses protect themselves by reviewing payment processes and alerting their accounting staff to this danger. The specifically advise the following:
- Verify changes in vendor payment location and confirm requests for transfer of funds.
- Be wary of free, web-based e-mail accounts, which are more susceptible to being hacked.
- Be careful when posting financial and personnel information to social media and company websites.
- Regarding wire transfer payments, be suspicious of requests for secrecy or pressure to take action quickly.
- Consider financial security procedures that include a two-step verification process for wire transfer payments.
- Create intrusion detection system rules that flag e-mails with extensions that are similar to company e-mail but not exactly the same. For example, .co instead of .com.
- If possible, register all Internet domains that are slightly different than the actual company domain.
- Know the habits of your customers, including the reason, detail, and amount of payments. Beware of any significant changes.
More information:
ShareSEP




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com