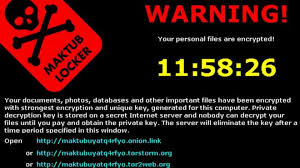
 Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at early ...
Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at early ...
AUG

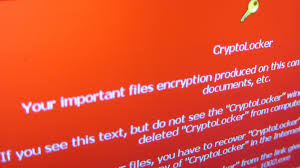 This week we will be focusing on preventing, detecting, and recovering from the many variants of the crypto-ransomware exploit. Ransomware attacks, such as CryptoLocker, CyrptoWall, Locky, Chimera, Zepto, and the like, have become one of the best money-making exploits for cyber-criminals, with new variants appearing on the scene every month. These attacks usually start with a phishing email and a ZIP file attachment or a malicious link, so email vigilance can ...
This week we will be focusing on preventing, detecting, and recovering from the many variants of the crypto-ransomware exploit. Ransomware attacks, such as CryptoLocker, CyrptoWall, Locky, Chimera, Zepto, and the like, have become one of the best money-making exploits for cyber-criminals, with new variants appearing on the scene every month. These attacks usually start with a phishing email and a ZIP file attachment or a malicious link, so email vigilance can ... Actually there are way more than ten ways, but here are some I see all the time. We can play this like a game, so go ahead and give yourself a point for each one of these that apply to you. This game scores like golf – low score wins.
Actually there are way more than ten ways, but here are some I see all the time. We can play this like a game, so go ahead and give yourself a point for each one of these that apply to you. This game scores like golf – low score wins. Should you hire a hacker? Recently, the US Department of Defense did just that in their
Should you hire a hacker? Recently, the US Department of Defense did just that in their  Many small businesses are being dragged into the arena of IT risk assessment by larger client companies, suppliers, or regulators. Common scenarios include credit card (PCI) or HIPAA compliance. Since the Target breach, smaller vendors and supplier companies who have a network connection into the IT operations of a larger company are being required to undergo the same sort of vulnerability and risk assessment ...
Many small businesses are being dragged into the arena of IT risk assessment by larger client companies, suppliers, or regulators. Common scenarios include credit card (PCI) or HIPAA compliance. Since the Target breach, smaller vendors and supplier companies who have a network connection into the IT operations of a larger company are being required to undergo the same sort of vulnerability and risk assessment ...
 Today is the 17th anniversary of the first
Today is the 17th anniversary of the first  I discovered a while ago that my LG smart phone can be used fairly easily to make a surreptitious video of a meeting simply by turning on the video camera and slipping the phone into a shirt pocket. The camera lens clears the edge of the pocket nicely, and there is no indication, at least on my phone, the the camera is rolling. This is a great way to keep a record ...
I discovered a while ago that my LG smart phone can be used fairly easily to make a surreptitious video of a meeting simply by turning on the video camera and slipping the phone into a shirt pocket. The camera lens clears the edge of the pocket nicely, and there is no indication, at least on my phone, the the camera is rolling. This is a great way to keep a record ... Sometimes in the maelstrom of cybersecurity battles, it is helpful to step back and see where we came from, where we are, and where we are going. This year, in addition to studying for and passing the CISSP exam, I have been to a bunch of security conferences. I’ve been to MISC.conf, Secure360, B-Sides, and the Tech Security Conference. Here are some highlights and ...
Sometimes in the maelstrom of cybersecurity battles, it is helpful to step back and see where we came from, where we are, and where we are going. This year, in addition to studying for and passing the CISSP exam, I have been to a bunch of security conferences. I’ve been to MISC.conf, Secure360, B-Sides, and the Tech Security Conference. Here are some highlights and ... Maybe you like the idea of two-factor authentication, but the Google Authenticator smartphone app seems too cumbersome. Or maybe you are not a smartphone owner, because you don’t like the idea of a phone that can track your location to within a few feet, and keeps sharing all your personal data with the apps on your phone. So you own a flip phone ...
Maybe you like the idea of two-factor authentication, but the Google Authenticator smartphone app seems too cumbersome. Or maybe you are not a smartphone owner, because you don’t like the idea of a phone that can track your location to within a few feet, and keeps sharing all your personal data with the apps on your phone. So you own a flip phone ...