 I am always mystified when clients of mine fall for fake tech support phone calls or browser pop-ups. Didn’t their Mom tell them not to talk to strangers? After all, they are my clients, shouldn’t they be calling me FIRST?
I am always mystified when clients of mine fall for fake tech support phone calls or browser pop-ups. Didn’t their Mom tell them not to talk to strangers? After all, they are my clients, shouldn’t they be calling me FIRST?
Naked Security reported on May 13th that Microsoft’s search service, Bing, will no longer accept advertising for online tech support companies. This is good news for everyone except the legitimate computer support ...
Continue Reading →JUN

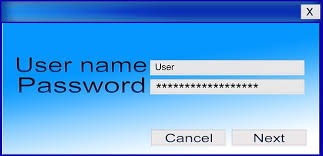 If I can get your user name and password, I can easily break into and use your computer and network resources just as if I were you. Bruce Schneier wrote an article recently that discussed this issue. Many of the largest exploits are started with
If I can get your user name and password, I can easily break into and use your computer and network resources just as if I were you. Bruce Schneier wrote an article recently that discussed this issue. Many of the largest exploits are started with 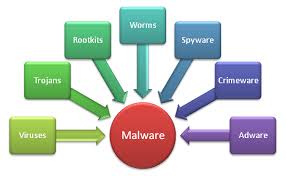 On Wednesday we looked at the obvious, visual symptoms of a malware infection. Today we will explore some changes in performance that can indicate that your computer is infected.
On Wednesday we looked at the obvious, visual symptoms of a malware infection. Today we will explore some changes in performance that can indicate that your computer is infected. A rare Tuesday post, but this is too important to wait. If you own a Lenovo computer, you need to uninstall the Lenovo Accelerator application. A recent
A rare Tuesday post, but this is too important to wait. If you own a Lenovo computer, you need to uninstall the Lenovo Accelerator application. A recent  Although my very first PC user experience was on an Apple IIe back in 1984, I have really been a Windows guy for the most part. Got on my first Windows PC back around 1991, and bought my first Windows PC (Windows 3.11) in 1994. I do have an iMac in my current computer collection. But lately I have been playing around more and more in the Linux platform, both Ubuntu ...
Although my very first PC user experience was on an Apple IIe back in 1984, I have really been a Windows guy for the most part. Got on my first Windows PC back around 1991, and bought my first Windows PC (Windows 3.11) in 1994. I do have an iMac in my current computer collection. But lately I have been playing around more and more in the Linux platform, both Ubuntu ... This is not a gripe about Spell-Check, although I
This is not a gripe about Spell-Check, although I 
 One of the very worst breaches that can happen to you is for an attacker to be able to access your email account. If someone else can access your email, and read the messages you send and receive, and access your contact list and calendar, then they can learn many personal details about you that would make it easier to steal your identity, access other web accounts using the password reset ...
One of the very worst breaches that can happen to you is for an attacker to be able to access your email account. If someone else can access your email, and read the messages you send and receive, and access your contact list and calendar, then they can learn many personal details about you that would make it easier to steal your identity, access other web accounts using the password reset ...