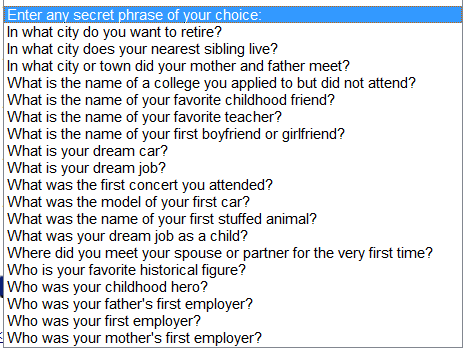
What if you could eliminate 95% of cybersecurity exploits by doing one thing better? Would you do it? Social Engineering in its many forms accounts for 95% to 99% of common exploits that cybercriminals use to gain initial access to your information assets. There are two simple security controls that you can put in place that would virtually eliminate the threats caused by social engineering.
What if you could eliminate 95% of cybersecurity exploits by doing one thing better? Would you do it? Social Engineering in its many forms accounts for 95% to 99% of common exploits that cybercriminals use to gain initial access to your information assets. There are two simple security controls that you can put in place that would virtually eliminate the threats caused by social engineering.
Social engineering is the use of deception, ...
Continue Reading →NOV