Phishing Email Alerts
Catch of the Day: Action Required Password Expired Phish
Chef’s Special: Google Drive Alert Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
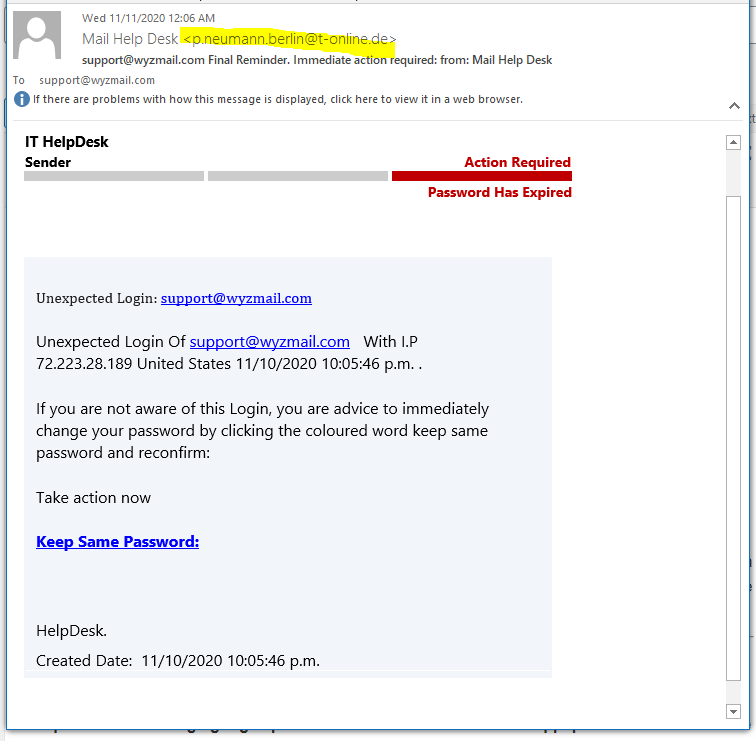
Action Required Password Expired
Nice little rhyme. This looked like a rather poorly done credential stealing exploit. The “login” page is a rather generic page that lacks the usual replica logos and trade dress of a better exploit. But it got fun when I found I was able to poke around in the web server of the attacker. This looks like a Malware as as Service exploit that was purchased on the Dark Web by a rather inexperienced attacker.
First the straightforward part. Below is the phishing email, with the usual weird sender address.
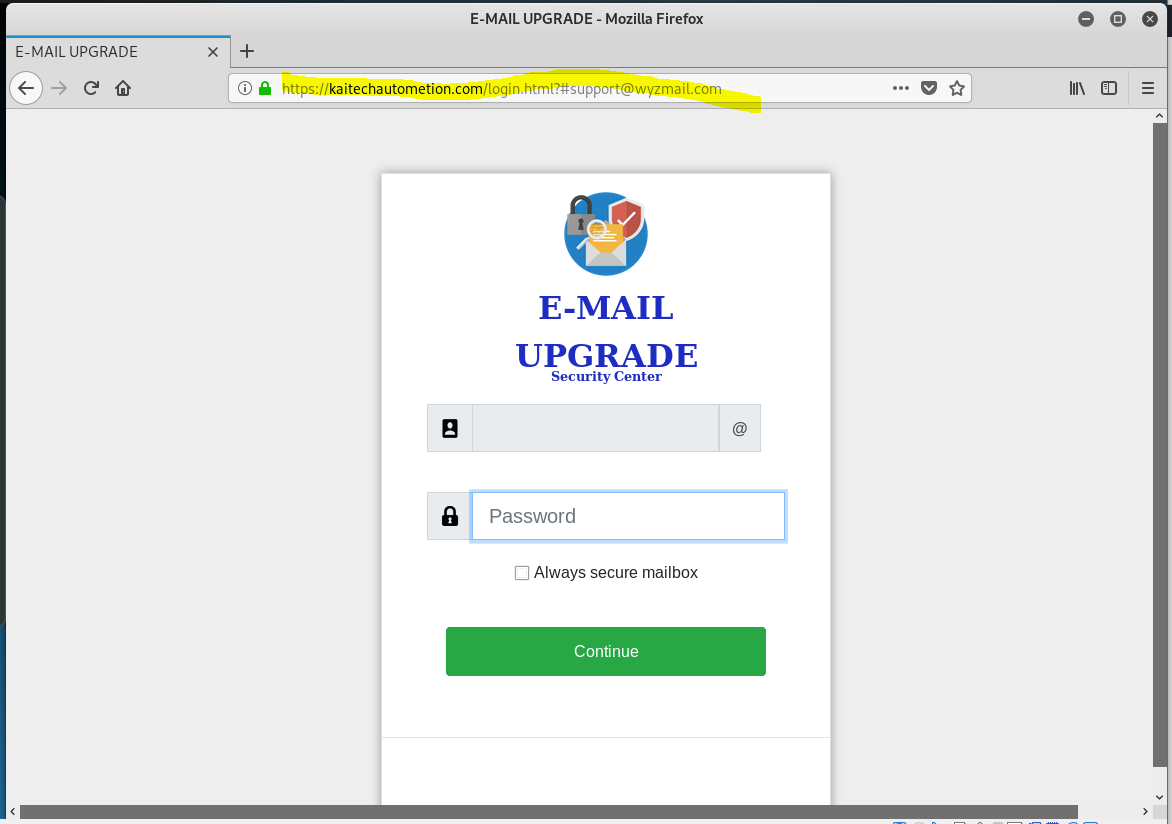
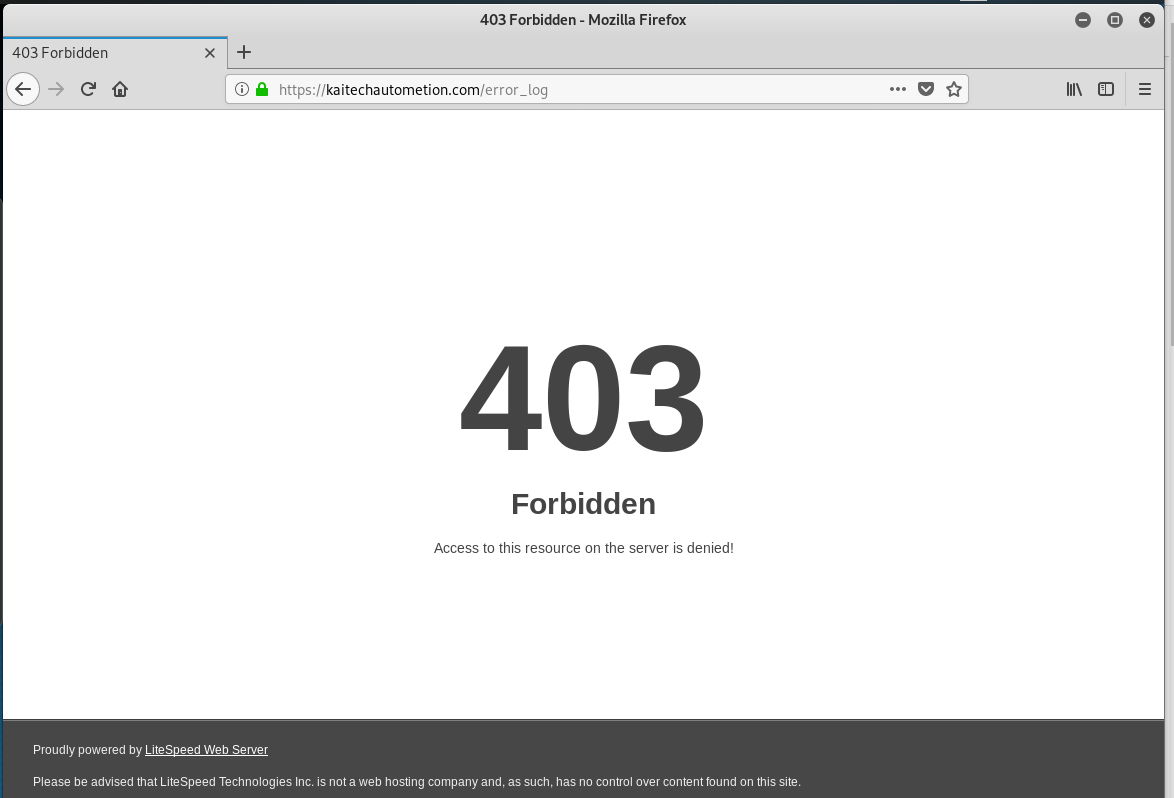
The Keep Same Password link resolves to https://kaitechautometion.com/login.html?#support@wyzmail.com with no further redirection. VirusTotal did not flag this link, I fired up my Kali Linux VM, and clicked on the link. The landing page is Proudly Served by LiteSpeed Web Server at kaitechautometion.com Port 443 according to the footer. The landing page below has a pretty generic login in form inviting me for an e-mail upgrade. Nothing to see here, or so I thought.
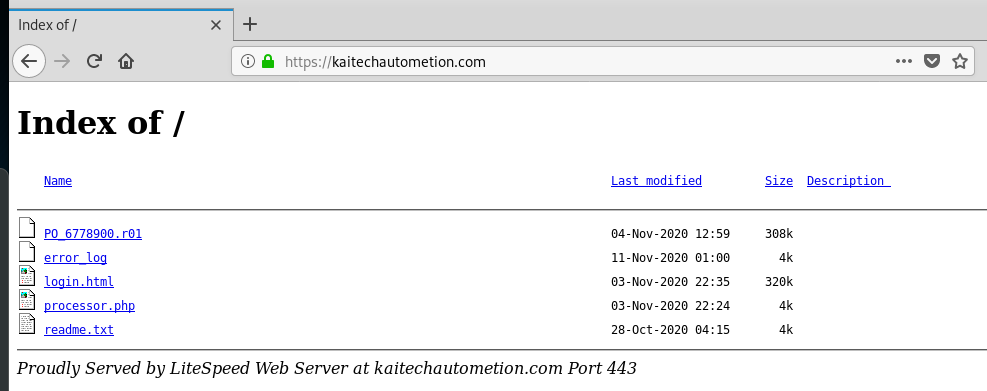
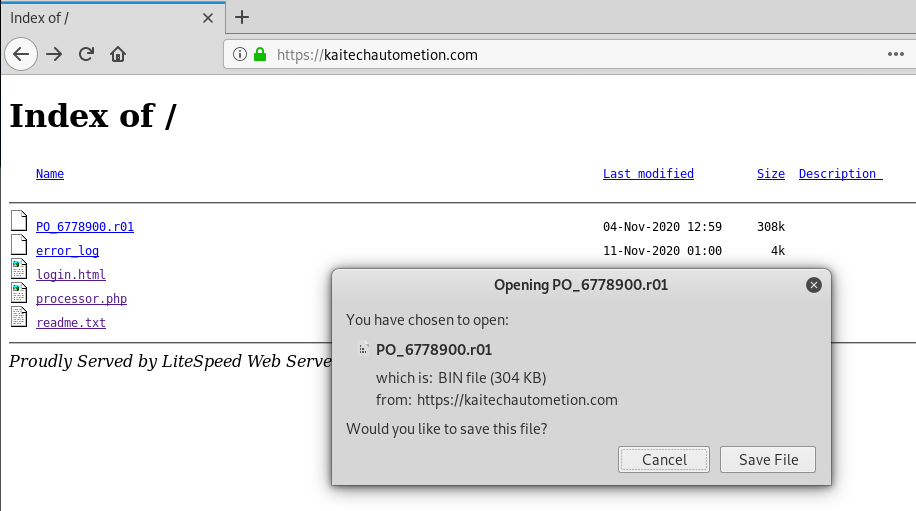
I decided to open the home page at kaitechautometion.com, to see if this was a hijacked website. I was given an index of page for a home page. This allowed me to browse around this guy’s web server.
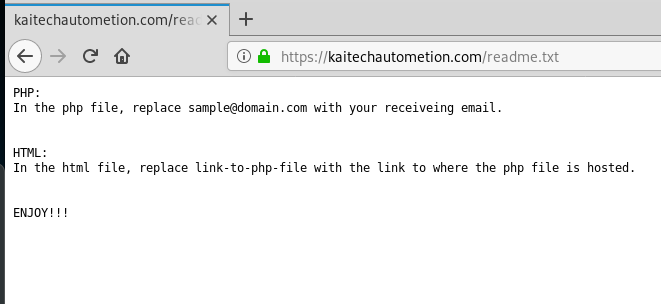
First to the readme.txt file. I got the impression from the “Enjoy!” comment that this is a purchased exploit kit. The lack of operational security has me guessing that this exploit is being run by a less experienced cyber-criminal. For instance, I should not be able to get inside this directory.
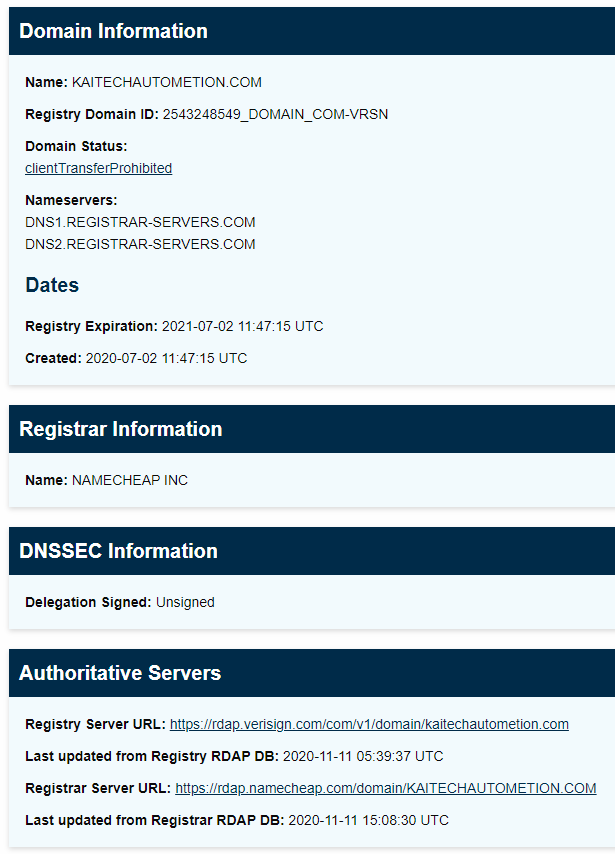
On to the error.log page. I keep seeing the banner Proudly Served by LiteSpeed Web Server at kaitechautometion.com Port 443, and have come to the conclusion that this exploit is being hosted on a public host using the attacker’s own account. Serious lapse in OPSEC again. My curiosity had me looking up the domain on ICAAN WHOIS. That information will be posted at the end.
The login.html link provided an image for the landing page. The only thing left was the P0_6778900.r01 link. Clicking here opened up a download screen.
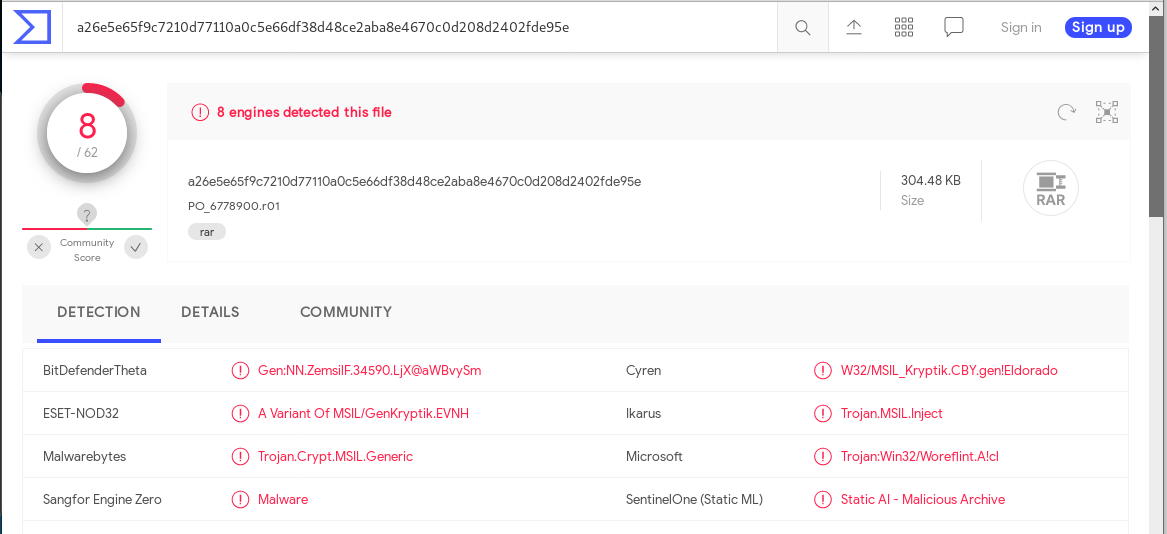
Again, using my Kali VM, (don’t try this at home, professional driver on closed course) I downloaded the file, and uploaded it to VirusTotal for analysis.
At VirusTotal, eight different scanning engines determined that this was the executable malware code, a variant of the Kryptic (MSIL) Trojan. I deleted the malicious file from Kali, and emptied the Trash for good measure.
As promised, the WHOIS information is below. The domain was registered in July of this year on Namecheap. Since the GDPR, no longer can you get Registrant information from WHOIS, which makes investigations like this one a bit harder.
New Phishing Links Sent Via Legitimate Google Drive Alert Emails
Scammers are abusing a Google Drive feature to send phishing links in automated email notifications from Google, WIRED reports. By mentioning a Google user in a Drive document, the scammers can cause Google to generate a notification that will be sent straight to the user’s inbox, bypassing spam filters.
“The smartest part of the scam is that the emails and notifications it generates come directly from Google,” they explain. “On mobile, the scam uses the collaboration feature in Google Drive to generate a push notification inviting people to collaborate on a document.
If tapped, the notification takes you directly to a document that contains a very large, tempting link. An email notification created by the scam, which also comes from Google, also contains a potentially malicious link. Unlike regular spam, which Gmail does a pretty good job of filtering out, this message not only makes it into your inbox, it gets an added layer of legitimacy by coming from Google itself.” Read entire article here And another article on Wired.
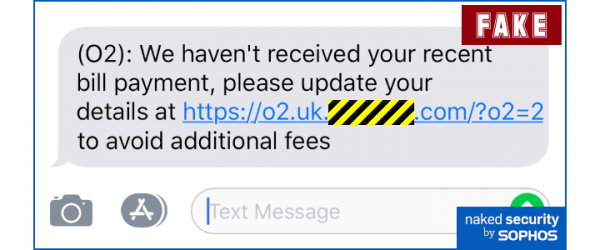
Smishing attack tells you “mobile payment problem” – don’t fall for it!
Don’t be fooled by a website that looks OK – it’s easy for crooks to make an exact copy. (This time, they got just one letter wrong.)
Share
NOV





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com