Thanks to my cousin Rick Weiss for this image. He plays for The Infected Cranberries.
Continue Reading →JUN
Thanks to my cousin Rick Weiss for this image. He plays for The Infected Cranberries.
Continue Reading → A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.World’s first and oldest cybercrime (1830) predates electrical telegraphy. Read how two French bond traders hacked France’s military semaphore telegraph.
With a name like BACKLASH, you might think this hack comes from the era of mechanical devices, with gears and pulleys. You’d be right!
In our last post we looked at the frighteningly short amount of time that it takes to crack a typical password. Today we will look at all the different password cracking methods that a clever attacker can use to compromise your password, and how to defend against these attacks.
There are several types of automated password attacks that can be combined to make the process quicker, or to configure for a certain type of password attack.
Did you know that the most popular passwords can be cracked in minutes? And that passwords with 8 characters or fewer can be cracked in a few seconds? This is why I say that passwords by themselves are no longer a useful form of security. Today is the second of a five part series on password security, and focuses on the methodology used by password cracking software programs.
Cyber-criminal groups who specialize in password cracking generally harvest huge lists of user ...
Continue Reading →I have said it before, and I will repeat it now: passwords by themselves are no longer a useful form of security. The only option that makes passwords secure is two-factor authentication. Today we embark on a two week investigation into passwords, why they are so easy to break, how your password might be compromised, and how to create a password system that is less vulnerable to exploitation.
Why are passwords so easy to crack? Some of the answers we have ...
Continue Reading →I just thought this was neat. Hope you enjoy it too. From the Smithsonian
Continue Reading → A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
Microsoft is a relatively new friend to open source, and their purchase of GitHub is causing considerable consternation to developers.
Read ...
Continue Reading →Have you ever wondered what happens to the location information your smartphone is collecting about you? Who has access to that information, and for what purpose? As it turns out, as told in a recent report by Brian Krebs, this information is available to pretty much anybody.
A related article in Sophos’ Naked Security blog pointed to a ...
Continue Reading → IoT or the Internet of Things has been to this point a seriously unsecured cluster-flop for the most part. Millions of insecure devices are in our homes and businesses, and these devices may be eavesdropped, recording audio or video, performing a DDoS attack, or being leveraged as an easy access pivot point into your network for further exploitation
IoT or the Internet of Things has been to this point a seriously unsecured cluster-flop for the most part. Millions of insecure devices are in our homes and businesses, and these devices may be eavesdropped, recording audio or video, performing a DDoS attack, or being leveraged as an easy access pivot point into your network for further exploitation
Thankfully, progress is being made ...
Continue Reading →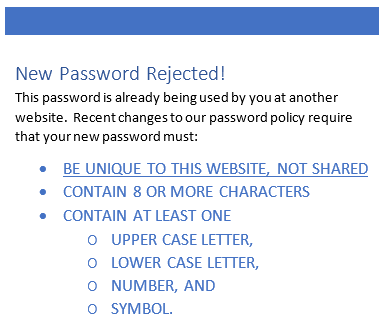 What do you think about a plan that would actually make it impossible for you to use the same password on two or more sites? Basically, when you set up a new web account, you would be forced to use a password that was truly different from other passwords you use elsewhere?
What do you think about a plan that would actually make it impossible for you to use the same password on two or more sites? Basically, when you set up a new web account, you would be forced to use a password that was truly different from other passwords you use elsewhere?
I am certain that if you are reading this blog, that ...
Continue Reading →