 What would it be like if you could identify yourself and authenticate your account by the way you type? A Romanian company, TypingDNA, has created a Chrome extension that does just that.
What would it be like if you could identify yourself and authenticate your account by the way you type? A Romanian company, TypingDNA, has created a Chrome extension that does just that.
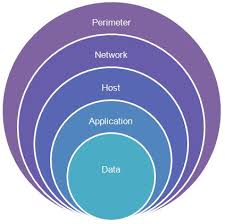
I am a big advocate of two-factor authentication, but there are some problems. One of the three types of authentication is biometrics, which is “something you are.” NIST, in SP 800-63B states ...
Continue Reading →MAR