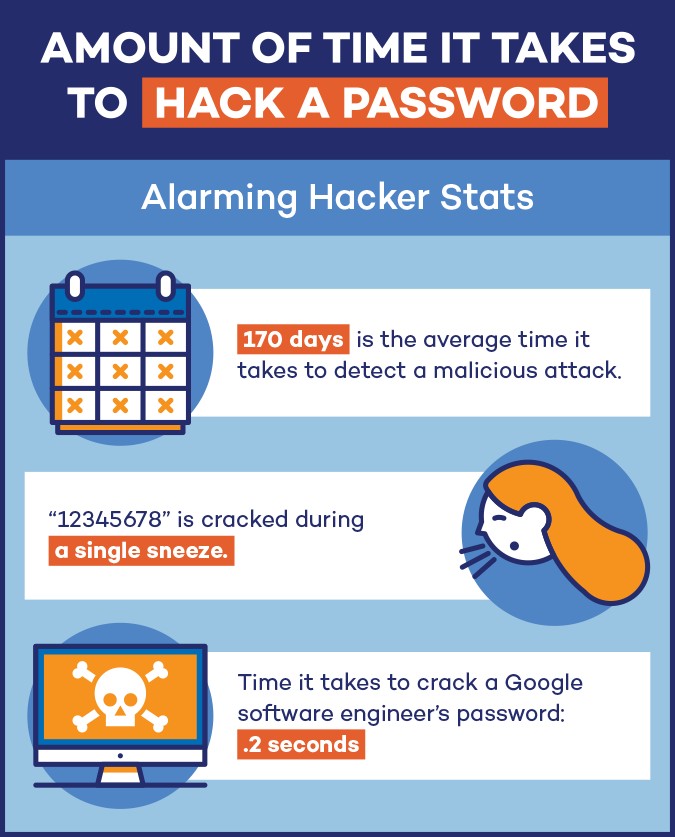
Did you know that the most popular passwords can be cracked in minutes? And that passwords with 8 characters or fewer can be cracked in a few seconds? This is why I say that passwords by themselves are no longer a useful form of security. Today is the second of a five part series on password security, and focuses on the methodology used by password cracking software programs.
Cyber-criminal groups who specialize in password cracking generally harvest huge lists of user IDs and passwords from database servers that support web site operations of the victim company. This is known as a “server breach.” Want to know if your password has been breached, then check out Troy Hunt’s have i been pwned website. Typically, these password lists are encrypted, but the password crackers have high speed powerful computers and software programs to use to try to guess all possible password combinations at are rate of several thousand guess per second.
If your attacker has targeted your company specifically, they will try to export the password database on the compromised system, or better yet, the Windows domain controller server. This is stored in the SAM file, which is also encrypted. The SAM file will be much smaller, usually several dozen to several hundred users, so these attackers typically use off the shelf computer hardware and software like “John the Ripper” to solve for plaintext passwords.
In either case, the software is not decrypting the password, because passwords are encrypted using a one-way encryption method called “hashing.” The software tries different hashing methods to hash all possible combinations of letters, numbers, and symbols to create their own table of password hashes. Any time a hash on their table matches a password hash from the stolen list, they have “solved” for the plaintext password.
The software is designed to go after the most common passwords first, then dictionary words, then variations of dictionary words, which is called a “dictionary attack,” and then everything else, which is called a “brute-force attack.” The dictionary attack can get solutions as quickly as .30 milliseconds. Passwords with fewer than 8 characters fall in a similar time frame. But 12 character passwords may take as long as several decades to solve.
Solved password lists can be purchased on the Dark Web. These lists are called “Rainbow Tables” and exist for password list of up to 10 characters or more. These pre-solved lists remove the necessity of rehashing everything yourself, and your software tools only need to do the comparison part, reducing the time it takes to solve your own list.
Cracked password lists can be purchased for any sub-group you are interested in. Only want Gmail accounts, they are for sale. Looking for email or network passwords at a specific business target? They may be available as well.
In our next post we will be looking at other ways that an attacker may acquire your password.
A special thanks to Panda Security for inspiring the content of this series and providing us with the infographics used in this series.
ShareJUN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com