 When you lose your login credentials to an online account, it can be devastating. Depending on what was compromised and what was lost, you may have an expensive and time-consuming task on your hands. So the bad guys took your user ID and password, or some other personal information. Was it worth it? There is an active resale market for this information, and some ...
When you lose your login credentials to an online account, it can be devastating. Depending on what was compromised and what was lost, you may have an expensive and time-consuming task on your hands. So the bad guys took your user ID and password, or some other personal information. Was it worth it? There is an active resale market for this information, and some ...
SEP

 We warned our readers about the
We warned our readers about the 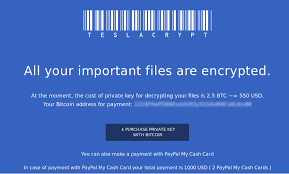 You have trained your staff and improved your defenses. In spite of your best efforts, you have an active case of crypto-malware running on a system in your business. How do you recover?
You have trained your staff and improved your defenses. In spite of your best efforts, you have an active case of crypto-malware running on a system in your business. How do you recover? Many small businesses are being dragged into the arena of IT risk assessment by larger client companies, suppliers, or regulators. Common scenarios include credit card (PCI) or HIPAA compliance. Since the Target breach, smaller vendors and supplier companies who have a network connection into the IT operations of a larger company are being required to undergo the same sort of vulnerability and risk assessment ...
Many small businesses are being dragged into the arena of IT risk assessment by larger client companies, suppliers, or regulators. Common scenarios include credit card (PCI) or HIPAA compliance. Since the Target breach, smaller vendors and supplier companies who have a network connection into the IT operations of a larger company are being required to undergo the same sort of vulnerability and risk assessment ... Sometimes in the maelstrom of cybersecurity battles, it is helpful to step back and see where we came from, where we are, and where we are going. This year, in addition to studying for and passing the CISSP exam, I have been to a bunch of security conferences. I’ve been to MISC.conf, Secure360, B-Sides, and the Tech Security Conference. Here are some highlights and ...
Sometimes in the maelstrom of cybersecurity battles, it is helpful to step back and see where we came from, where we are, and where we are going. This year, in addition to studying for and passing the CISSP exam, I have been to a bunch of security conferences. I’ve been to MISC.conf, Secure360, B-Sides, and the Tech Security Conference. Here are some highlights and ... Maybe you like the idea of two-factor authentication, but the Google Authenticator smartphone app seems too cumbersome. Or maybe you are not a smartphone owner, because you don’t like the idea of a phone that can track your location to within a few feet, and keeps sharing all your personal data with the apps on your phone. So you own a flip phone ...
Maybe you like the idea of two-factor authentication, but the Google Authenticator smartphone app seems too cumbersome. Or maybe you are not a smartphone owner, because you don’t like the idea of a phone that can track your location to within a few feet, and keeps sharing all your personal data with the apps on your phone. So you own a flip phone ... Google Authenticator is my favorite go-to app for setting up two-factor authentication. But what if you want to remove an account from Google Authenticator?
Google Authenticator is my favorite go-to app for setting up two-factor authentication. But what if you want to remove an account from Google Authenticator? One of the easiest ways for an intruder to learn about you is through a compromised email account. And since most email is transmitted in the clear or in plain text, it is a simple thing for a bad actor to read intercepted email traffic. Encrypting your email makes it harder for criminals, competitors, law enforcement, and government spy agencies to read your email messages.
One of the easiest ways for an intruder to learn about you is through a compromised email account. And since most email is transmitted in the clear or in plain text, it is a simple thing for a bad actor to read intercepted email traffic. Encrypting your email makes it harder for criminals, competitors, law enforcement, and government spy agencies to read your email messages. Using copy and paste to save text from websites is something all of us commonly do. Nothing could be simpler, right? Highlight your text, then <ctrl> c, and <ctrl> v. It turns out that this can be dangerous.
Using copy and paste to save text from websites is something all of us commonly do. Nothing could be simpler, right? Highlight your text, then <ctrl> c, and <ctrl> v. It turns out that this can be dangerous. On Wednesday we discussed the many, many ways your smartphone is vulnerable to attack. Today we will look at solutions. Smart mobile devices need to be secured just as you would a laptop or desktop computer The small size and easy portability of smartphones and tablets make them easier to steal or lose. Some of our recommendations:
On Wednesday we discussed the many, many ways your smartphone is vulnerable to attack. Today we will look at solutions. Smart mobile devices need to be secured just as you would a laptop or desktop computer The small size and easy portability of smartphones and tablets make them easier to steal or lose. Some of our recommendations: