 How would you feel if, in order to gain access to a known terrorist’s house, the government passed a law that required every lock manufacturer to create a master key that would unlock every locked door anywhere? What if the police promised that they would only use the key on the one house? What if they promised to keep the key safe and secure so it could never get into the hands ...
How would you feel if, in order to gain access to a known terrorist’s house, the government passed a law that required every lock manufacturer to create a master key that would unlock every locked door anywhere? What if the police promised that they would only use the key on the one house? What if they promised to keep the key safe and secure so it could never get into the hands ...
MAR

 A great product for quickly and easily adding web site filtering to your organization is OpenDNS Umbrella. OpenDNS was recently purchased by Cisco Systems. OpenDNS is another featured security product that is part of the Managed Services program here at
A great product for quickly and easily adding web site filtering to your organization is OpenDNS Umbrella. OpenDNS was recently purchased by Cisco Systems. OpenDNS is another featured security product that is part of the Managed Services program here at  Try to imagine how much bad stuff we could keep off our computers and networks if we could figure out a way to filter incoming traffic from the Dark Web. Well maybe we can.
Try to imagine how much bad stuff we could keep off our computers and networks if we could figure out a way to filter incoming traffic from the Dark Web. Well maybe we can. This should really be called “anti-social” engineering. A good definition is “social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter.”
This should really be called “anti-social” engineering. A good definition is “social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter.”
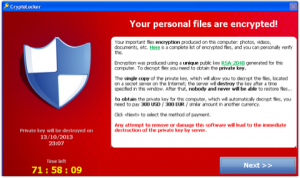 This is hot off the press. Yesterday
This is hot off the press. Yesterday  A virtual private network, or VPN, is a type of network computer connection that creates a private encrypted communications channel, commonly called a “tunnel,” when using insecure networks, such as in hotels and coffee shops, or when communicating over the Internet. Many businesses provide a VPN connection for their mobile and traveling employees. This means that when out of the office, a worker can open the VPN and be connected to ...
A virtual private network, or VPN, is a type of network computer connection that creates a private encrypted communications channel, commonly called a “tunnel,” when using insecure networks, such as in hotels and coffee shops, or when communicating over the Internet. Many businesses provide a VPN connection for their mobile and traveling employees. This means that when out of the office, a worker can open the VPN and be connected to ... Quick answer: Yes it can! A
Quick answer: Yes it can! A  Passwords – Is mine strong enough? How do I know? Every time I write a password article I feel as if this subject has already been done to death by me and others. But I always get more positive feedback on this subject than others I consider more interesting, so we offer the following suggestions:
Passwords – Is mine strong enough? How do I know? Every time I write a password article I feel as if this subject has already been done to death by me and others. But I always get more positive feedback on this subject than others I consider more interesting, so we offer the following suggestions: As we approach the new year it is traditional to make our New Year’s Resolutions. Unfortunately, most resolutions are made but not kept, so I am a little reluctant to offer these ideas for improving your cybersecurity in the coming year. But if you have not climbed on the cybersecurity bandwagon yet, you are definitely overdue. Pick a few of these ideas to implement in your business.
As we approach the new year it is traditional to make our New Year’s Resolutions. Unfortunately, most resolutions are made but not kept, so I am a little reluctant to offer these ideas for improving your cybersecurity in the coming year. But if you have not climbed on the cybersecurity bandwagon yet, you are definitely overdue. Pick a few of these ideas to implement in your business.