Tuesday we get to vote for president again. Worried about the security of electronic voting machines? You are not alone, but you would not find any political or election officials in your group. They think everything is fine! The fact that your next president may be elected by the Russian Cyber Army is OK, I guess. So that means Trump.
Here’s a little humor to make the nightmare seems more acceptable.
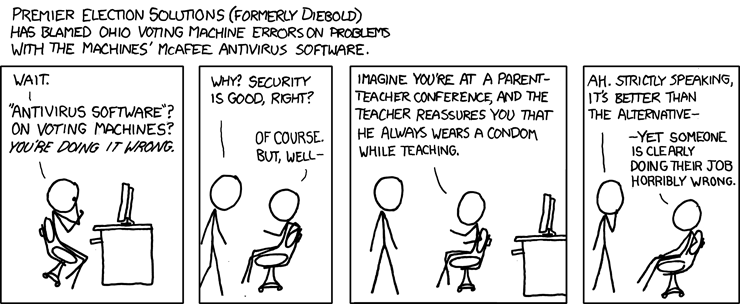 Continue Reading →
Continue Reading →
NOV

 A couple of weeks ago I attended the Minneapolis Cyber Security Summit 2016 at the J.W. Marriot Hotel in Bloomington Minnesota. There were two days of presentations on cybersecurity issues, and here are a few of the takeaways for small and medium sized business owners.
A couple of weeks ago I attended the Minneapolis Cyber Security Summit 2016 at the J.W. Marriot Hotel in Bloomington Minnesota. There were two days of presentations on cybersecurity issues, and here are a few of the takeaways for small and medium sized business owners. In the last several days, we have seen big distributed denial of service (DDoS) attacks against DynDNS, an Internet services company that provides domain name services (DNS) to many companies including Twitter and PayPal. DNS is how web sites are found on the web, you enter a web address in your browser, and DNS finds the website you are looking for. When attacked in ...
In the last several days, we have seen big distributed denial of service (DDoS) attacks against DynDNS, an Internet services company that provides domain name services (DNS) to many companies including Twitter and PayPal. DNS is how web sites are found on the web, you enter a web address in your browser, and DNS finds the website you are looking for. When attacked in ... NIST has created a self assessment tool for companies and organization who are working through the
NIST has created a self assessment tool for companies and organization who are working through the  US-CERT sent out an announcement in September about a new video from the FTC for people whose personal information may have been breached in a cyber incident. There are tips on reporting, and how to recover with tools such as a credit freeze or fraud alert. There are many links on both the
US-CERT sent out an announcement in September about a new video from the FTC for people whose personal information may have been breached in a cyber incident. There are tips on reporting, and how to recover with tools such as a credit freeze or fraud alert. There are many links on both the 
 Years ago I heard a story about someone on a job interview was asked by the hiring manager for the user ID and password to their Facebook account. My response, then and now, was “sure – but you first.” The idea being if you want to know that much about my personal life, then I want to know the same about you. Maybe ...
Years ago I heard a story about someone on a job interview was asked by the hiring manager for the user ID and password to their Facebook account. My response, then and now, was “sure – but you first.” The idea being if you want to know that much about my personal life, then I want to know the same about you. Maybe ... We were interviewed again by Sarah Westall on her web radio show
We were interviewed again by Sarah Westall on her web radio show  We have written about Stuxnet a couple of times. (
We have written about Stuxnet a couple of times. ( The National Institute for Standards and Technology is working on new password guidelines which will be mandated for government sector users, and strongly recommended for businesses as well. Still in draft from, the standards can be found on the document
The National Institute for Standards and Technology is working on new password guidelines which will be mandated for government sector users, and strongly recommended for businesses as well. Still in draft from, the standards can be found on the document