 The House Judiciary Committee’s Encryption Working Group has released a report that comes out in favor of strong encryption, and opposed to the daft notion of creating encryption “backdoors” for law enforcement and government to use. As we have expressed in this blog previously, the concept that the secret backdoor keys could somehow be kept securely, when nothing else seems to be able to be kept secret, is the main fatal ...
The House Judiciary Committee’s Encryption Working Group has released a report that comes out in favor of strong encryption, and opposed to the daft notion of creating encryption “backdoors” for law enforcement and government to use. As we have expressed in this blog previously, the concept that the secret backdoor keys could somehow be kept securely, when nothing else seems to be able to be kept secret, is the main fatal ...
JAN

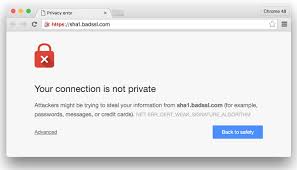 SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged.
SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged. The answer to this question is complicated, but not impossible to understand. The first thing to know is that most passwords are not cracked by guessing, or trying thousands of possibilities one at a time on a typical login screen. Most systems will lock the account after a certain small number of failed attempts, like 5 or 6. This makes the kind of ...
The answer to this question is complicated, but not impossible to understand. The first thing to know is that most passwords are not cracked by guessing, or trying thousands of possibilities one at a time on a typical login screen. Most systems will lock the account after a certain small number of failed attempts, like 5 or 6. This makes the kind of ... As we approach year-end, many small and medium sized business owners and managers are coming to the realization that their best intentions for creating a cybersecurity program in their organization have fallen short. This was the year, you promised yourself, that we get a handle on computer and network security.
As we approach year-end, many small and medium sized business owners and managers are coming to the realization that their best intentions for creating a cybersecurity program in their organization have fallen short. This was the year, you promised yourself, that we get a handle on computer and network security. A couple of weeks ago I attended the Minneapolis Cyber Security Summit 2016 at the J.W. Marriot Hotel in Bloomington Minnesota. There were two days of presentations on cybersecurity issues, and here are a few of the takeaways for small and medium sized business owners.
A couple of weeks ago I attended the Minneapolis Cyber Security Summit 2016 at the J.W. Marriot Hotel in Bloomington Minnesota. There were two days of presentations on cybersecurity issues, and here are a few of the takeaways for small and medium sized business owners. When I am doing a cybersecurity presentation, someone is bound to ask about the Dark Web. What is it, exactly, and how does someone get there? The how part we discussed on Friday.
When I am doing a cybersecurity presentation, someone is bound to ask about the Dark Web. What is it, exactly, and how does someone get there? The how part we discussed on Friday.  You don’t need to be a journalist, freedom fighter, or living under an oppressive political regime to have the desire for some online privacy. Maybe you are trying to put the contents of your life back into the Pandora’s box you opened when you signed up on Facebook. Maybe you would like a little privacy in your online life.
You don’t need to be a journalist, freedom fighter, or living under an oppressive political regime to have the desire for some online privacy. Maybe you are trying to put the contents of your life back into the Pandora’s box you opened when you signed up on Facebook. Maybe you would like a little privacy in your online life. As we add more mobile and portable devices to our digital collection, cybersecurity for mobile devices becomes more important. Smartphones, tablets, wearable tech, and ultra-portable laptops are certainly convenient and easy to carry, but that makes them easy for a thief to carry off. When these devices are stolen, you lose much more than the hardware. Every bit of information on the device is up for grabs too, from contact lists, personal information, ...
As we add more mobile and portable devices to our digital collection, cybersecurity for mobile devices becomes more important. Smartphones, tablets, wearable tech, and ultra-portable laptops are certainly convenient and easy to carry, but that makes them easy for a thief to carry off. When these devices are stolen, you lose much more than the hardware. Every bit of information on the device is up for grabs too, from contact lists, personal information, ... Holy acronyms Batman! What the heck does this headline mean? Well, the National Institute for Standards and Technology (NIST) has removed two-factor authentication (TFA) via short-messaging service (SMS) from the approved list of two-factor authentication methods. The reason is that SMS is an unencrypted service, and the lack of encryption makes it too insecure for use in Federal authentication systems. NIST is recommending that all ...
Holy acronyms Batman! What the heck does this headline mean? Well, the National Institute for Standards and Technology (NIST) has removed two-factor authentication (TFA) via short-messaging service (SMS) from the approved list of two-factor authentication methods. The reason is that SMS is an unencrypted service, and the lack of encryption makes it too insecure for use in Federal authentication systems. NIST is recommending that all ... I am a firm believer in, and user of two-factor authentication (TFA or 2FA). Heck, if there was three-factor authentication I would probably sign up. The two most popular authenticator apps are Authy and Google Authenticator. I primarily use Google Authenticator wherever I can. I use SMS when Authenticator isn’t an option, or won’t work. I had trouble, for instance, getting Facebook to work ...
I am a firm believer in, and user of two-factor authentication (TFA or 2FA). Heck, if there was three-factor authentication I would probably sign up. The two most popular authenticator apps are Authy and Google Authenticator. I primarily use Google Authenticator wherever I can. I use SMS when Authenticator isn’t an option, or won’t work. I had trouble, for instance, getting Facebook to work ...