 SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged.
SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged.
SHA-1 is used in common services such as SSL (secure websites) and TLS (secure email). There has been discussion about the low security of SHA-1 going back to 2005. In 2010 the National Institute for Standards and Technology has recommended that government agencies stop using SHA-1. And in 2014, Google stated it would actively penalize websites still using SHA-1 in SSL certificates after 2016. The reason is that the hash length is considered too short to be be absolutely secure. The recommended upgrade path is to SHA-2 or SHA-3.
When I am performing vulnerability assessments for client companies, SHA-1 vulnerabilities show up often. Upgrading would eliminate those vulnerabilities. And now we have other reasons to move on from SHA-1 implementations. Next year, Google, Microsoft, Apple, and Mozilla browsers will no longer accept SHA-1 connections.
- Microsoft Internet Explorer and Edge: Starting on February 14, IE and Edge will not load any websites still using SHA-1, though users can still opt to continue to the website after seeing a warning message.
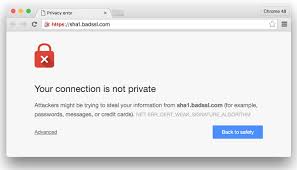
- Google Chrome: At the end of January next year, with the release of version 56, Chrome will stop trusting any SHA-1 SSL certificate and will provide a security warning.
- Mozilla Firefox: With the release of Firefox 51 in January, the browser will show an “untrusted connection” error warning for any site still using SHA-1.
- Apple Safari: Apple is strongly suggesting sites to drop SHA-1 as soon as possible, and websites loaded in the Sierra version do not show the green padlock that indicates a trusted site.
If you are using a SHA-1 SSL certificate on your website, you will want to upgrade to something better as soon as possible, or risk running your visitors through the gauntlet of worrisome security warnings, not to mention lower Google page rank. If you have manually created self-signed security certificates on your Windows computer network, you will need to go through the process of updating those certificates to SHA-2 or 3.
More information:
ShareDEC




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com