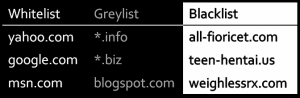
This is reprinted from an email I received from the Libertarian Party on Monday August 24th.
Cryptocurrency has been on an historic run in recent days, reaching heights not seen in years and positioning itself as a hedge against economic uncertainty to rival more traditional safe harbors like gold and silver. As central banks continue printing off ream after ream of fiat currency, the ...
Continue Reading →AUG