By Aaron Smith
Criminals will eventually find vulnerabilities and exploit them. Unsecure virtual meetings are no exception
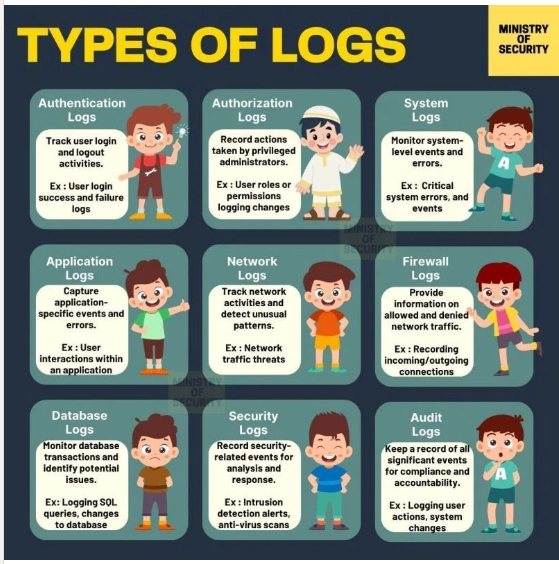
Companies conduct hundreds of thousands of virtual meetings every day. Many of these meetings include the exchanging of sensitive information that could damage the company if it fell into the wrong hands. Cybercriminals are aware of this and will do everything in their power to access it. Luckily, video conferencing providers are fighting back by equipping their software with end-to-end encryption
Here’s how it works.
From Sender ...
Continue Reading →MAR