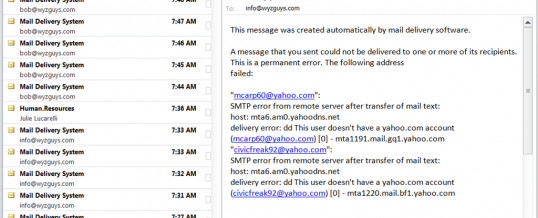
This has happened to me a couple of times, and I always get panicked calls from clients when it happens to them. All of a sudden your email inbox is flooded with undeliverable return email messages, sent to people you have never heard of. Hundreds of them, spanning sometimes as much as a week’s time. See below.
Has your email account been hacked? Do you have to change your password? In a word, NO. You are merely the victim of “spoofing,” ...
Continue Reading →JAN








![windowsdefender_lead_w_180[1] windowsdefender_lead_w_180[1]](http://wyzguyscybersecurity.com/wp-content/uploads/2014/12/windowsdefender_lead_w_180-25255B1-25255D_thumb.jpg)