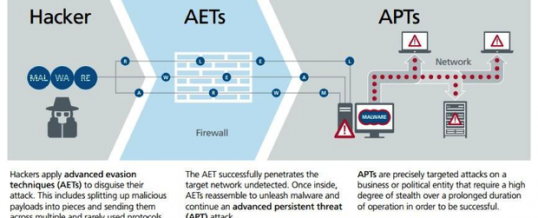
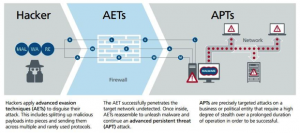
If you are using any of these excuses in your business you are likely already in trouble. Don’t say we didn’t warn you!
- I’m too small to be a target. Sorry, but false. Small and medium size businesses are seen as prime targets by my cyber-crime organizations just because they are usually poorly defended, easy to hack, and have assets worth the effort. If you have cash in a bank account, that can be enough to attract an attack.
- Internet security ...
OCT