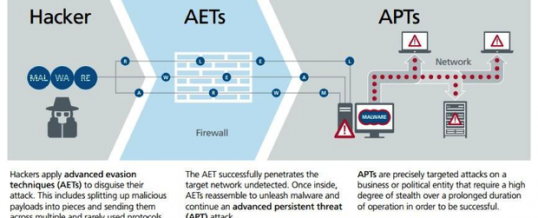
In a previous article we discussed a bit about how Advanced Persistent Threats (APT) were making network defense more challenging for cybersecurity professionals. A recent article on TechRepbulic takes a look at how Advanced Evasion Techniques (AET) are being used by cyber attackers to make APTs harder to discover.
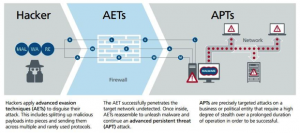
The illustration shows how AETs work, by cutting the exploit code into smaller pieces (fragmentation) and sending them on unexpected ports (obfuscation) in order to pass through perimeter defenses, and then reassemble once inside the victim network to begin the exploit. The Tech republic article references another PDF download from McAfee that goes into deeper detail. Both articles are a great read if you are tasked with managing network security for your organization.
The McAfee article states:
“There are millions of working combinations and permutations of AETs that may alter form during
attacks,” said Pat Calhoun, senior vice president of network security for McAfee. “This is why traditional
signature or pattern-match detection, the methods used by the majority of today’s network security
solutions, cannot effectively combat AETs.”
McAfee has a free tool called Evader which can be used by organizations to uncover evidence of AETs on their network.
ShareOCT




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com