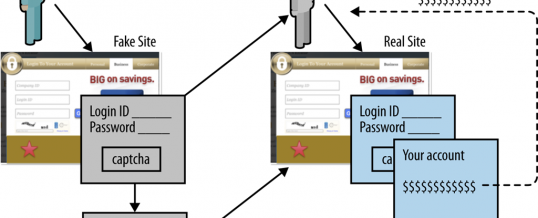
Cybercriminals have lots of ways to exploit their victims, but the single most effect method to gain initial entry remains the phishing email. If you want to protect yourself from these sorts of exploits you need to know what they look like and what happens if they trick you into responding. Let’s take a look at a scenario where the bad guys are trying to get your online banking credentials.
- Step 1: Cybercriminals will send out a realistic looking but fake ...
NOV