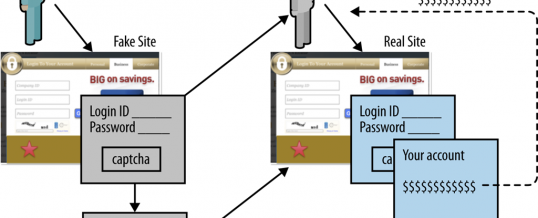
Cybercriminals have lots of ways to exploit their victims, but the single most effect method to gain initial entry remains the phishing email. If you want to protect yourself from these sorts of exploits you need to know what they look like and what happens if they trick you into responding. Let’s take a look at a scenario where the bad guys are trying to get your online banking credentials.
- Step 1: Cybercriminals will send out a realistic looking but fake email from “your bank.” Always wearing perfect trade dress, using the bank’s logo and usual typeface, these emails generally contain a message that explains a problem with your account, asking you to click on the provided link. There almost always is some sort of penalty for failing to comply with their request. So look for this pattern: the problem, the link, the veiled threat, almost every phishing email I’ve seen contains all three. Most people will ignore these sorts of messages, but there are always a few that click through on the provided link.
- Bonus solution: Never ever click on the provided link. Go to your banking website the way you always do, by opening your web browser and using the Favorite or Bookmark you always use, or typing in the web address manually.
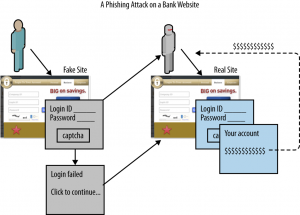
- Step 2: If you click on the link, you will be taken to a perfect replica of your banking login page. This will be visually identical to your regular login page. It may even include a CAPTCHA code. When you enter your user name and password and the CAPTCHA solution, and click on Submit, your banking credentials are sent to the cybercriminals.
- Step 3: Here is where it gets interesting. You will be shown an “oops” screen explaining that there was an error with the user name, password, or CAPTCHA, and a link or button to click to try again. This link actually redirects the victim to their bank’s actual login page.
- Step 4: On the second attempt, the account holder successfully logs into the real banking web site. They see their account balances are as they should be, and they think they are safe.
- Step 5: With the captured user name and password in hand, the cyber-thieves log into the account later, and transfer the money to other accounts that they control. The victim is now been separated from their money, and most banks will simply shrug their shoulders sympathetically, and offer to “do what we can” but the money is gone, and you are not getting it back.
Late in September, the was a significant breach of customer information at JP Morgan Chase bank (JP Morgan Chase confirms breach, 76 million homes and 7 million businesses affected) was reported, and what this for certain is that Chase customers can expect phishing attacks just like the one described here.
So when you get those emails from your bank, be suspicious and check it out without clicking on the provided link. Go directly to the bank web site, or here’s an old school idea – give them a call! a little vigilance and a healthy dose of suspicion is all it takes to keep your bank account safe from phishing attacks.
And here’s a link to an article that describes a novel DropBox phishing scam. In this exploit, the victim receives an email that says there is a file waiting for them on DropBox that is too big to email. When the victims click on the link, they see a fake DropBox login page that is actually hosted on DropBox in the cybercriminal’s account. Then they are encourage to log in using their Gmail, Outlook.com, Facebook, LinkedIn, or Yahoo account credentials. Those logins are then captured by the cybertheives for later reuse. This is how they hijack your online accounts.
Image courtesy of MAPR
ShareNOV




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com