 DARPA (Defense Advanced Research Projects Agency) recently held a contest to explore the feasibility of automating the process of finding vulnerabilities on a group of target computers, and automatically fixing the vulnerabilities. Using a game format similar to “capture the flag,” on Aug. 5,at the Paris Las Vegas hotel, seven teams of programmers, hackers and researchers set a cybersecurity milestone.
DARPA (Defense Advanced Research Projects Agency) recently held a contest to explore the feasibility of automating the process of finding vulnerabilities on a group of target computers, and automatically fixing the vulnerabilities. Using a game format similar to “capture the flag,” on Aug. 5,at the Paris Las Vegas hotel, seven teams of programmers, hackers and researchers set a cybersecurity milestone.
According to Darpa “Our best data ...
Continue Reading →AUG

 Here is a short list of applications that I use frequently when undertaking a penetration test of vulnerability scan. I don’t use all of these all the time, but they are probably the most popular tools in the security community. We start with Kali, the Swiss Army knife of exploitation tools. What can’t Kali do? Then we look several stand alone tools for host enumeration, port scanning, packet sniffing, vulnerability detection, ...
Here is a short list of applications that I use frequently when undertaking a penetration test of vulnerability scan. I don’t use all of these all the time, but they are probably the most popular tools in the security community. We start with Kali, the Swiss Army knife of exploitation tools. What can’t Kali do? Then we look several stand alone tools for host enumeration, port scanning, packet sniffing, vulnerability detection, ... Not sure how funny this is. According to
Not sure how funny this is. According to  Holy acronyms Batman! What the heck does this headline mean? Well, the National Institute for Standards and Technology (NIST) has removed two-factor authentication (TFA) via short-messaging service (SMS) from the approved list of two-factor authentication methods. The reason is that SMS is an unencrypted service, and the lack of encryption makes it too insecure for use in Federal authentication systems. NIST is recommending that all ...
Holy acronyms Batman! What the heck does this headline mean? Well, the National Institute for Standards and Technology (NIST) has removed two-factor authentication (TFA) via short-messaging service (SMS) from the approved list of two-factor authentication methods. The reason is that SMS is an unencrypted service, and the lack of encryption makes it too insecure for use in Federal authentication systems. NIST is recommending that all ... I am a firm believer in, and user of two-factor authentication (TFA or 2FA). Heck, if there was three-factor authentication I would probably sign up. The two most popular authenticator apps are Authy and Google Authenticator. I primarily use Google Authenticator wherever I can. I use SMS when Authenticator isn’t an option, or won’t work. I had trouble, for instance, getting Facebook to work ...
I am a firm believer in, and user of two-factor authentication (TFA or 2FA). Heck, if there was three-factor authentication I would probably sign up. The two most popular authenticator apps are Authy and Google Authenticator. I primarily use Google Authenticator wherever I can. I use SMS when Authenticator isn’t an option, or won’t work. I had trouble, for instance, getting Facebook to work ...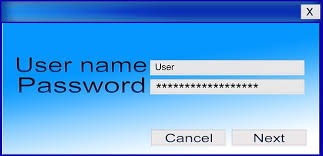 Bruce Schneier had an
Bruce Schneier had an 
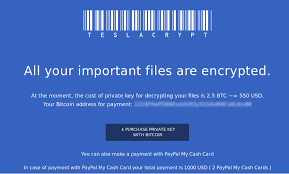 You have trained your staff and improved your defenses. In spite of your best efforts, you have an active case of crypto-malware running on a system in your business. How do you recover?
You have trained your staff and improved your defenses. In spite of your best efforts, you have an active case of crypto-malware running on a system in your business. How do you recover?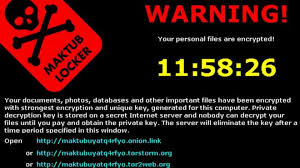 Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at ...
Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at ...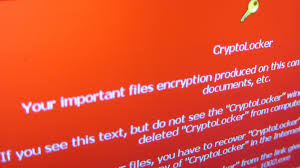 This week we will be focusing on preventing, detecting, and recovering from the many variants of the crypto-ransomware exploit. Ransomware attacks, such as CryptoLocker, CyrptoWall, Locky, Chimera, Zepto, and the like, have become one of the best money-making exploits for cyber-criminals, with new variants appearing on the scene every month. These attacks usually start with a phishing email and a ZIP file attachment or a malicious link, so email vigilance can ...
This week we will be focusing on preventing, detecting, and recovering from the many variants of the crypto-ransomware exploit. Ransomware attacks, such as CryptoLocker, CyrptoWall, Locky, Chimera, Zepto, and the like, have become one of the best money-making exploits for cyber-criminals, with new variants appearing on the scene every month. These attacks usually start with a phishing email and a ZIP file attachment or a malicious link, so email vigilance can ...