Happy Birthday to the Father of Our Country!
Continue Reading →FEB
 If you are an Apple user, Apple released a number of updates released late in January that will fix security vulnerabilities in several platforms and services. It was reported by US-CERT on January 23rd.
If you are an Apple user, Apple released a number of updates released late in January that will fix security vulnerabilities in several platforms and services. It was reported by US-CERT on January 23rd.
The release for Mac OSX Sierra is large, at 105 GB, and fixes many holes that would allow and attacker to remotely execute malware. This is something you should fix ...
Continue Reading → NIST is working on new authentication standards, and there are some surprising changes coming out of this effort. One of the issues that NIST is dealing with is the use of biometrics for authentication. But there are problems with biometrics. Here they are from the NIST Special Publication 800-63b. Emphasis is mine.
NIST is working on new authentication standards, and there are some surprising changes coming out of this effort. One of the issues that NIST is dealing with is the use of biometrics for authentication. But there are problems with biometrics. Here they are from the NIST Special Publication 800-63b. Emphasis is mine.
For a variety of reasons, ...
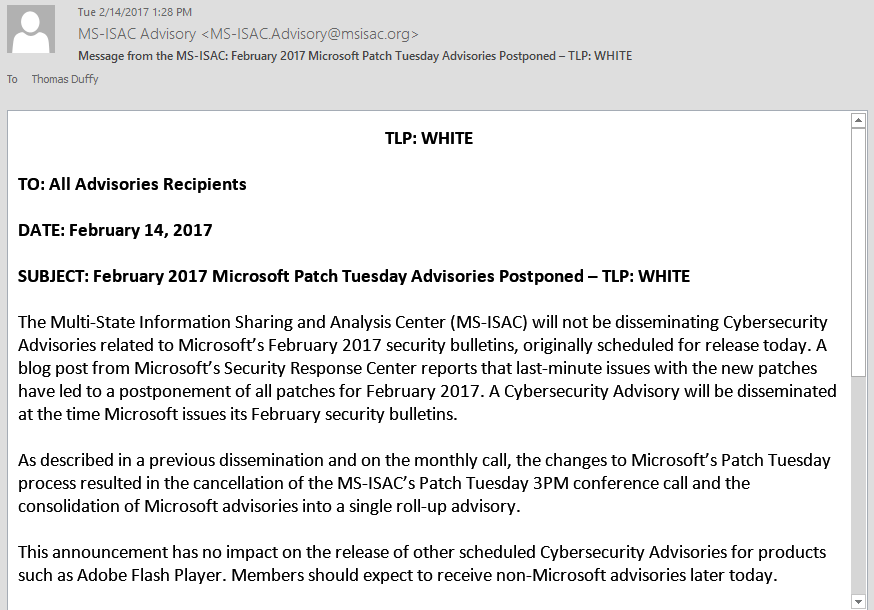
Continue Reading →Wow. Microsoft discovered some last minute issues with February’s Patch Tuesday update, and cancelled them. You can read about it on TechNet. They will be reissued at a later date, after suitable repairs are made.
As a user who had occasionally found myself on the wrong end of an update that caused my computer to misbehave, all I can say is “Thank you Microsoft.”
 Continue Reading →
Continue Reading →
 Passwords are not dead – not yet. But they are on life support. They are no longer enough to truly secure anything on their own.
Passwords are not dead – not yet. But they are on life support. They are no longer enough to truly secure anything on their own.
I just read an sobering, eye-popping article on NetMux that discussed easy ways to crack passwords that are longer than 12 characters.
What makes this so disheartening for me is that I have been telling everyone to increase their password ...
Continue Reading →With Valentine’s Day around the corner, I thought this post from Pinterest was an interesting origin story.

 On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims.
On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims.
This exploit uses a phishing email to send the target either a PDF attachment or a Word attachment. The PDF variant uses Windows Powershell to install. ...
Continue Reading → I read a story in Naked Security recently that reported the arrest of a couple of Italian cyber-criminals who have been stealing personal information from Italian mayors, prime ministers, cardinals, and other notables since 2010. They used a phishing exploit to install a Trojan Horse/keylogger called EyePyramid. There were a couple of things that caught my eye.
I read a story in Naked Security recently that reported the arrest of a couple of Italian cyber-criminals who have been stealing personal information from Italian mayors, prime ministers, cardinals, and other notables since 2010. They used a phishing exploit to install a Trojan Horse/keylogger called EyePyramid. There were a couple of things that caught my eye.
The first is the sheer volume of data stolen – 87 gigabytes! This information ...
Continue Reading → Opera Neon is an interesting new experimental project from Opera. They are giving the browser a new look that resembles your computer’s desktop. There are new controls which makes working with tabs and organizing your windows more natural. There is a video pop-out feature which lets you view the video in one part of your screen while continuing to use the browser for other things. The change to visual tabs is ...
Opera Neon is an interesting new experimental project from Opera. They are giving the browser a new look that resembles your computer’s desktop. There are new controls which makes working with tabs and organizing your windows more natural. There is a video pop-out feature which lets you view the video in one part of your screen while continuing to use the browser for other things. The change to visual tabs is ...