Seems to be a busy summer so far. Barely finished up with WannaCry and now we are dealing with Petya. Here are some useful links
Seems to be a busy summer so far. Barely finished up with WannaCry and now we are dealing with Petya. Here are some useful links
About Petya:
- Barkly blog
- Sophos Naked Security blog
- US-CERT
- Another from US-CERT Good prevention, detection, and mitigation information.
- Microsoft SMBv1 Vulnerability
- Microsoft Security Bulletin MS17-010 run this update NOW if you haven’t already.
I have followed with great interest the ...
Continue Reading →JUN

 This is the time of the year everyone writes either a year in review article, or a what’s coming in the new year post. Guess which one this is? I’ve been reading the pundits, and considering my own findings as a cybersecurity professional. I pulled together the following list for your review, and to help you plan where to spend your time, talent, and budget in 2017.
This is the time of the year everyone writes either a year in review article, or a what’s coming in the new year post. Guess which one this is? I’ve been reading the pundits, and considering my own findings as a cybersecurity professional. I pulled together the following list for your review, and to help you plan where to spend your time, talent, and budget in 2017.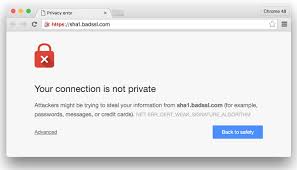 SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged.
SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged. We were interviewed again by Sarah Westall on her web radio show
We were interviewed again by Sarah Westall on her web radio show  We have written about Stuxnet a couple of times. (
We have written about Stuxnet a couple of times. ( This is not a new story, and I decided not to write about it when this “sale” of pilfered NSA hacking tools was offered last August by a group identified as the
This is not a new story, and I decided not to write about it when this “sale” of pilfered NSA hacking tools was offered last August by a group identified as the