 One of the hardest types of phishing emails to defend against are those that come from the email account of a friend or trusted business associate, such as your dentist, lawyer, realtor. The sender’s email address is not spoofed, because the malefactor has tricked them into providing their email address password. The bad guys are actually logged into your friend’s email account, and now they are trying to do the same thing to you.
One of the hardest types of phishing emails to defend against are those that come from the email account of a friend or trusted business associate, such as your dentist, lawyer, realtor. The sender’s email address is not spoofed, because the malefactor has tricked them into providing their email address password. The bad guys are actually logged into your friend’s email account, and now they are trying to do the same thing to you.
If ...
Continue Reading →DEC

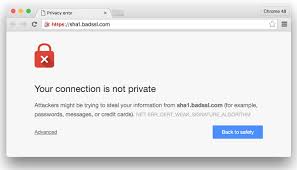 SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged.
SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged. On Monday we attacked the utility of current password policies and standards. Today we will offer up an array of improvements.
On Monday we attacked the utility of current password policies and standards. Today we will offer up an array of improvements. Most corporate password policies are a waste off time and do not add anything extra to providing secure authentication. Many of these policies were put in place to meet the standards of various compliance bodies (PCI-DSS, HIPAA, etc.) But basically these policies are not keeping up with the state of the art in password cracking, as we discussed last November in our post on ...
Most corporate password policies are a waste off time and do not add anything extra to providing secure authentication. Many of these policies were put in place to meet the standards of various compliance bodies (PCI-DSS, HIPAA, etc.) But basically these policies are not keeping up with the state of the art in password cracking, as we discussed last November in our post on ... It was recently reported in Naked Security that a Seattle television news crew interviewed an Office Depot employee who alerted them to the practice of selling in-store repair scams to customers who came in looking for computer help. This whistle-blower told a story where employees where encouraged and even pressured to run the chain’s “PC Health Check” on evey ...
It was recently reported in Naked Security that a Seattle television news crew interviewed an Office Depot employee who alerted them to the practice of selling in-store repair scams to customers who came in looking for computer help. This whistle-blower told a story where employees where encouraged and even pressured to run the chain’s “PC Health Check” on evey ... The answer to this question is complicated, but not impossible to understand. The first thing to know is that most passwords are not cracked by guessing, or trying thousands of possibilities one at a time on a typical login screen. Most systems will lock the account after a certain small number of failed attempts, like 5 or 6. This makes the kind of ...
The answer to this question is complicated, but not impossible to understand. The first thing to know is that most passwords are not cracked by guessing, or trying thousands of possibilities one at a time on a typical login screen. Most systems will lock the account after a certain small number of failed attempts, like 5 or 6. This makes the kind of ... We have Black Friday coming at the end of this week, and Cyber Monday next week. A lot of money will be changing hands between now and Christmas. We want to make sure that you are not a victim of some cyber-criminal’s Merry Christmas purchases with your money. A safe and secure shopping experience both online and in person can be yours if you follow some simple tips:
We have Black Friday coming at the end of this week, and Cyber Monday next week. A lot of money will be changing hands between now and Christmas. We want to make sure that you are not a victim of some cyber-criminal’s Merry Christmas purchases with your money. A safe and secure shopping experience both online and in person can be yours if you follow some simple tips: As we approach year-end, many small and medium sized business owners and managers are coming to the realization that their best intentions for creating a cybersecurity program in their organization have fallen short. This was the year, you promised yourself, that we get a handle on computer and network security.
As we approach year-end, many small and medium sized business owners and managers are coming to the realization that their best intentions for creating a cybersecurity program in their organization have fallen short. This was the year, you promised yourself, that we get a handle on computer and network security. The Mirai and Bashlight botnets have caused quite a stir in the cybersecurity and IT realms. The easy ability to round up and deploy millions of devices in a botnet using automated tools has raised the bar. How we respond to DDoS attacks will have to change.
The Mirai and Bashlight botnets have caused quite a stir in the cybersecurity and IT realms. The easy ability to round up and deploy millions of devices in a botnet using automated tools has raised the bar. How we respond to DDoS attacks will have to change. I was tempted to post this article late in October, when Brian Krebs suffered with the DDoS attack on his website, or when the Mirai botnet attack on DynDNS was in full swing, but decided to wait it out until after the election, in case it turns out that the Dyn attack was a precursor to an attack to disrupt the elections. And as of today, it appears that it was ...
I was tempted to post this article late in October, when Brian Krebs suffered with the DDoS attack on his website, or when the Mirai botnet attack on DynDNS was in full swing, but decided to wait it out until after the election, in case it turns out that the Dyn attack was a precursor to an attack to disrupt the elections. And as of today, it appears that it was ...