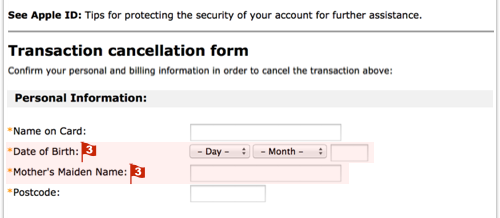
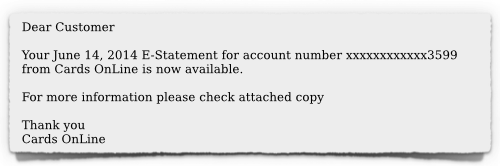
I just read an article on Sophos that shows all the steps in a typical phishing exploit. The example they used was a spoofed iTunes scam, where the attackers warn you that unauthorized persons are buying songs on your account. If you really want to learn how to spot and avoid these threats, you should make the click over to their site. But basically the exploits starts with an email (as many of them do.)
Continue Reading →The red flags in ...
AUG