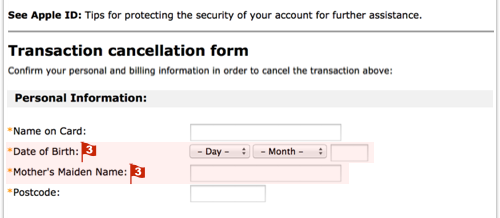
I just read an article on Sophos that shows all the steps in a typical phishing exploit. The example they used was a spoofed iTunes scam, where the attackers warn you that unauthorized persons are buying songs on your account. If you really want to learn how to spot and avoid these threats, you should make the click over to their site. But basically the exploits starts with an email (as many of them do.)
The red flags in this email are:
- Hovering over the link reveals a URL that is clearly unrelated to Apple. We have redacted it here, but it is a URL on a legitimate website that seems to have been hacked.
- The From and Reply to addresses are unrelated to Apple and unlikely for any official email. (But be careful: the text that is displayed as the sender’s address is part of the email itself, so a careful crook can make it look as legitimate as he wants.)
- It’s not the AppStore, it’s the App Store.
- Apple can verify your password, but not recover it. The company never stores your raw password, so it can’t send it to you, and would never imply that it could.
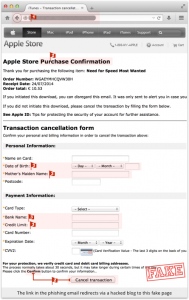 Clicking through the links with take you to a hacked legitimate web site where a fake but realistic iTunes Store lives to take your user ID and password, and credit card information, and forward it along to the scammers. The illustrations and explanations in the article show how easily a person can be tricked by these types of exploits.
Clicking through the links with take you to a hacked legitimate web site where a fake but realistic iTunes Store lives to take your user ID and password, and credit card information, and forward it along to the scammers. The illustrations and explanations in the article show how easily a person can be tricked by these types of exploits.
My rule of thumb: never click on a link in an email without confirming the destination. This can be accomplished by hovering on the link without clicking until the tool tip windows opens. Then examine the web address to be sure you are really going to the correct web site and not something that is spoofed. You can check links on VirusTotal as well.
Better yet just manually enter the web address of the company, or go to your web site using your own saved bookmark, favorite, or shortcut.
The other rule: These emails always make it sound like something scary is happening and/or you are losing money. Or sometimes it is the deal that is just too good to be true. Learn to be skeptical. Doubt and challenge these messages. If there is a problem on your account you should be able to see that is true simply by going directly to the site on your own. (See above)
ShareAUG




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com