From Pinterest. I know its says Canadian, but this works for my peeps too. Like the time I took my family to California for Christmas. We rented a convertible. Drove with the top down. All the parka clad Californians thought we were bizarre. Hey, it was 50 degrees! Plenty warm enough.
 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
WordPress users – do an update now, and do it by hand!
The automatic update to WordPress 4.9.3 broke automatic updating, so the emergency update to 4.9.4 means you need to click a button.
Babies’ data being sold ...
Continue Reading →FEB
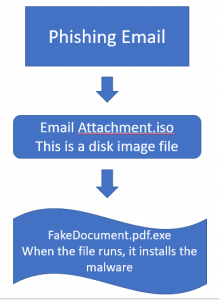 There is a new email attachment exploit making the rounds, that uses a file type called a disk image. The file extension for this kind of file is ISO. ISO files are not inherently dangerous, and in the exploit work much the same way that a ZIP attachment works. This file type can sneak past email security filters because it is generally seen as ...
There is a new email attachment exploit making the rounds, that uses a file type called a disk image. The file extension for this kind of file is ISO. ISO files are not inherently dangerous, and in the exploit work much the same way that a ZIP attachment works. This file type can sneak past email security filters because it is generally seen as ...
FEB
 What if cyber-criminals or enemy nations could take over the computer control systems that run electric utilities, water systems, or traffic control systems for traffic lights and commuter trains. The effects could be disastrous.
What if cyber-criminals or enemy nations could take over the computer control systems that run electric utilities, water systems, or traffic control systems for traffic lights and commuter trains. The effects could be disastrous.
We have written about these systems before. These are known as SCADA (supervisory control and data acquisition) or ICS (industrial control systems). One of the claims of the industries that use SCADA systems is that they are ...
Continue Reading →FEB
 Registering common misspellings of popular website domain names is a big business. A recent study found that 80% of all possible one-character typographical variants of Facebook, Google, and Apple are registered. Registering close misspellings of domain names is know as “typosquatting.”
Registering common misspellings of popular website domain names is a big business. A recent study found that 80% of all possible one-character typographical variants of Facebook, Google, and Apple are registered. Registering close misspellings of domain names is know as “typosquatting.”
Security company Sophos recently analysed all the possible one-letter variations of six popular websites, a whopping 2249 unique site names. Of the 2249 possibilities, 67% or 1502 domain names were actually registered. ...
Continue Reading →FEB
Since we take an interested in AI and robotics in this blog, the following church sign seemed a good candidate for Sunday Funnies. The most recent articles on the subjects of AI and “machine learning” seem to be saying the threat of AI is overblown, and is no match for the abstract reasoning prowess of human intelligence. This sign brings us a sobering wake up call.
From Pinterest
FEB
 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
Tax Identity Theft Awareness Week
File early or an impostor may get your refund. Especially now that the Equifax credit trove is in the wild.
01/29/2018 08:27 AM EST Original release date: January 29, 2018
Tax Identity Theft Awareness Week is January ...
Continue Reading →FEB
 If your business accepts credit cards for payment, then your a subject to the regulations of the Payment Card Industry. This is known as PCI-DSS Compliance. PCI compliance company Security Metrics recently released an infographic that shows the main compliance failures that lead to credit card breaches in 2017. Here are some of the startling take-aways:
If your business accepts credit cards for payment, then your a subject to the regulations of the Payment Card Industry. This is known as PCI-DSS Compliance. PCI compliance company Security Metrics recently released an infographic that shows the main compliance failures that lead to credit card breaches in 2017. Here are some of the startling take-aways:
- Businesses that took credit ...
FEB
 When you see the secure HTTPS protocol at the beginning of a web address, or see the green “secure site” padlock symbol, does this mean that the site is safe? Unfortunately, the answer is NO. There is some confusion among computer users about what HTTPS really means. This confusion is being exploited by cyber-criminals running phishing exploits.
When you see the secure HTTPS protocol at the beginning of a web address, or see the green “secure site” padlock symbol, does this mean that the site is safe? Unfortunately, the answer is NO. There is some confusion among computer users about what HTTPS really means. This confusion is being exploited by cyber-criminals running phishing exploits.
HTTPS or secure hypertext ...
Continue Reading →JAN
 The rare Tuesday post to advise about an impending event. Tomorrow there is a triple lunar event. A blue moon, which is when the moon appears twice in the same calendar month, a super moon, which is when the moon is closest in its rather wobbly orbit around the earth, and a blood moon, which is a lunar eclipse event when the moon passes through earth’s shadow, and the color ...
The rare Tuesday post to advise about an impending event. Tomorrow there is a triple lunar event. A blue moon, which is when the moon appears twice in the same calendar month, a super moon, which is when the moon is closest in its rather wobbly orbit around the earth, and a blood moon, which is a lunar eclipse event when the moon passes through earth’s shadow, and the color ...
JAN


