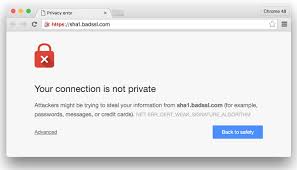
 SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged.
SHA-1 or Secure Hashing Algorithm 1 was developed in 1993 by the National Security Agency (NSA). It has been used to provide both hashing functions and digital signatures that validate that a certain document, web site, or other resource is genuine, original, and unchanged.
SHA-1 is used in common services such as SSL (secure websites) and TLS (secure email). There has been discussion about the low security of SHA-1 going back to 2005. ...
Continue Reading →DEC

 I will be a featured presenter at the MN Blogger Conference, on Saturday October 15, at Concordia University in St.Paul, from 8:15 am to 5:15 pm. Tickets are $20.
I will be a featured presenter at the MN Blogger Conference, on Saturday October 15, at Concordia University in St.Paul, from 8:15 am to 5:15 pm. Tickets are $20.
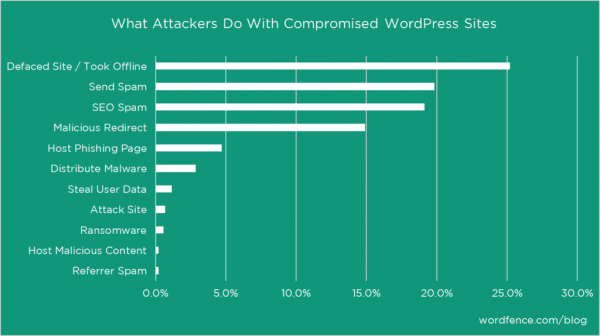

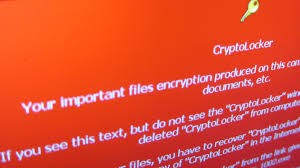 Some of the nastiest exploits going around are the many variants of the CryptoLocker and CryptoWall malware that encrypt all your personal files and hold them for ransom. Payment in bitcoin is required, in amounts starting at $200 and ranging upward to the $17,000 (400 BTC) that Hollywood Presbyterian Hospital just paid to unlock their files. Or even more. The amount will be whatever the attackers think they can extract from the victim.
Some of the nastiest exploits going around are the many variants of the CryptoLocker and CryptoWall malware that encrypt all your personal files and hold them for ransom. Payment in bitcoin is required, in amounts starting at $200 and ranging upward to the $17,000 (400 BTC) that Hollywood Presbyterian Hospital just paid to unlock their files. Or even more. The amount will be whatever the attackers think they can extract from the victim.