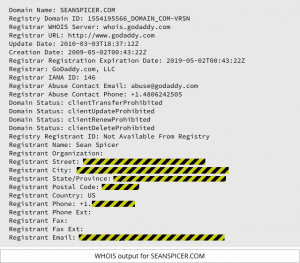
 I will start out by admitting that I hate Domain Privacy. But I just read a story in Naked Security on February 9th that is causing me to reevaluate my opinion. It turns out that the new White House press secretary, Sean Spicer, has a personal website at www.seanspicer.com. The website has been turned into a private site, but the WHOIS record ...
I will start out by admitting that I hate Domain Privacy. But I just read a story in Naked Security on February 9th that is causing me to reevaluate my opinion. It turns out that the new White House press secretary, Sean Spicer, has a personal website at www.seanspicer.com. The website has been turned into a private site, but the WHOIS record ...
FEB

 I read an interesting article on Naked Security the other day about how Hamas had used Facebook and social engineering tactics to trick Israeli soldiers into installing surveillance malware. The malware allowed Hamas to track the soldiers using the phone’s GPS, and to turn on the microphone and video to actually listen in and and watch their targets. Hamas undoubtedly picked up the ...
I read an interesting article on Naked Security the other day about how Hamas had used Facebook and social engineering tactics to trick Israeli soldiers into installing surveillance malware. The malware allowed Hamas to track the soldiers using the phone’s GPS, and to turn on the microphone and video to actually listen in and and watch their targets. Hamas undoubtedly picked up the ... As a regular reader of this blog, you are probably using a long, unique, 20 character password with two-factor authentication, and a password manager to keep it all straight. But let’s say that you fall for a phishing scam, and give away the password to your email account. The attacker can now use your email account to request password reset emails from your other online accounts, and you have yourself one ...
As a regular reader of this blog, you are probably using a long, unique, 20 character password with two-factor authentication, and a password manager to keep it all straight. But let’s say that you fall for a phishing scam, and give away the password to your email account. The attacker can now use your email account to request password reset emails from your other online accounts, and you have yourself one ...
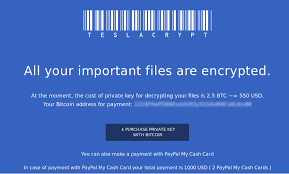 Crypto-ransomware continues to be one of the most popular money making exploits for cyber criminals. The reason for this is simple; its works, and the return on investment is quite high. According to a recent article in
Crypto-ransomware continues to be one of the most popular money making exploits for cyber criminals. The reason for this is simple; its works, and the return on investment is quite high. According to a recent article in  The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC.
The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC. On Monday we attacked the utility of current password policies and standards. Today we will offer up an array of improvements.
On Monday we attacked the utility of current password policies and standards. Today we will offer up an array of improvements.