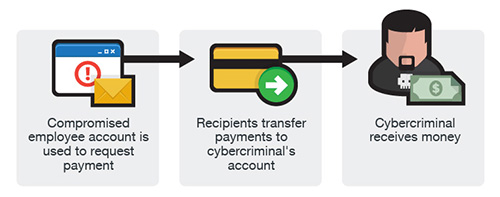
Your Personally Identifiable Information (PII) is one of the top targets of cyber-criminals. This information is valuable because it can be used for identity, fraud, tax refund fraud, loans and credit card applications, money transfers, phishing and spam campaigns, blackmail and extortion, fraudulent medical insurance claims, online shopping, and so much more. This information is packaged and sold on the Dark Web, and ...
Your Personally Identifiable Information (PII) is one of the top targets of cyber-criminals. This information is valuable because it can be used for identity, fraud, tax refund fraud, loans and credit card applications, money transfers, phishing and spam campaigns, blackmail and extortion, fraudulent medical insurance claims, online shopping, and so much more. This information is packaged and sold on the Dark Web, and ...
NOV