 Phishing is getting better and harder to detect. One new trend is using hijacked business email accounts to pivot further into a business, by using the built in trust of the company’s email domain to send phishing emails that appear to come from coworkers. These phishing emails from trusted sources are used to hijack other email accounts in the same company. This techniques is called lateral phishing.
Phishing is getting better and harder to detect. One new trend is using hijacked business email accounts to pivot further into a business, by using the built in trust of the company’s email domain to send phishing emails that appear to come from coworkers. These phishing emails from trusted sources are used to hijack other email accounts in the same company. This techniques is called lateral phishing.
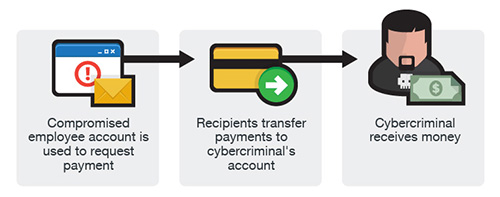
As I discussed in yesterday’s post, the FBI calls this business email compromise, or BEC. This is the number one cyber-crime in terms of dollars lost by the victims. It is also an alarmingly easy way for an attacker to profile a company employee, learn about the names of coworkers, suppliers and vendors, and customers or clients of the targeted business. As an attacker moves laterally through an email domain, they are able to gather more information and determine where the company’s proprietary information and financial resources are located.
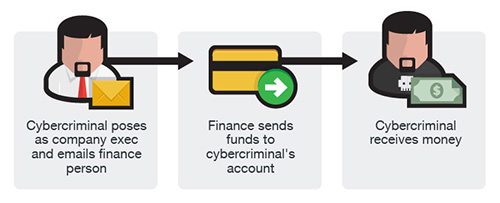 Often the victim’s email credentials are also used for network login credentials, and this gives the attacker the same network access as the victim. The attacker will attempt to move laterally through the organization, and once the email accounts of the CEO, CFO, and other highly placed managers are compromised, they can send authentic looking emails that appear to come from the boss. This makes exploits such as wire transfer fraud, payroll fraud, invoicing fraud, and interception of payments to the company much easier to set up. It also makes it easier to access company data files on file servers, and exfiltrate sensitive information, sometimes by sending them as file attachments in an email from a hijacked email account. This also makes it easier to distribute ransomware attacks and other malware exploits throughout the company.
Often the victim’s email credentials are also used for network login credentials, and this gives the attacker the same network access as the victim. The attacker will attempt to move laterally through the organization, and once the email accounts of the CEO, CFO, and other highly placed managers are compromised, they can send authentic looking emails that appear to come from the boss. This makes exploits such as wire transfer fraud, payroll fraud, invoicing fraud, and interception of payments to the company much easier to set up. It also makes it easier to access company data files on file servers, and exfiltrate sensitive information, sometimes by sending them as file attachments in an email from a hijacked email account. This also makes it easier to distribute ransomware attacks and other malware exploits throughout the company.
Lateral phishing works because cybersecurity defenses such as spam filters and email gateways often are configured to treat mail on the company’s email domain as trusted. These devices are filtering email coming into the email system from outside the organization, but are not looking at email that is moving within the organization. That way, phishing emails sent from compromised internal email accounts often go unchallenged. At that point, it is up to the recipient to detect the fraudulent email, but when it appears to originate from a coworker, the recipient usually complies with whatever request is in the email.
Beating lateral phishing takes some effort on the part of the information security team. Here are some effective countermeasures:
- Training – Let your staff known about this new threat. Send an informational email to all your employees, and include this exploit as a part of your next regular quarterly cybersecurity awareness training event.
- Email filter configuration – If you are not doing so already, reconfigure your email filter or gateway to scan internal emails for spam, phishing, and other anomalous behavior. All email should be suspected and scanned, regardless of where it is originated.
- Two-factor authentication – Here is another great use case for 2FA. Using 2FA for network logins and email logins will make it much more difficult or impossible for an attacker to hijack a user account or email account, much less move laterally through the email domain.
- Data loss prevention – Your DLP system should be set up to detect confidential data leaving the business through email attachments from the internal email domain.
These additional security controls should make it difficult to penetrate your email system through phishing emails and account compromise techniques. One more task to add to your cybersecurity to do list, but it will definitely be worth the effort.
ShareJUL




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com