 One of the very worst breaches that can happen to you is for an attacker to be able to access your email account. If someone else can access your email, and read the messages you send and receive, and access your contact list and calendar, then they can learn many personal details about you that would make it easier to steal your identity, access other web accounts using the password reset process, ...
One of the very worst breaches that can happen to you is for an attacker to be able to access your email account. If someone else can access your email, and read the messages you send and receive, and access your contact list and calendar, then they can learn many personal details about you that would make it easier to steal your identity, access other web accounts using the password reset process, ...
MAY




 Keith Graham of SecureAuth was recently interviewed for a recent article on
Keith Graham of SecureAuth was recently interviewed for a recent article on 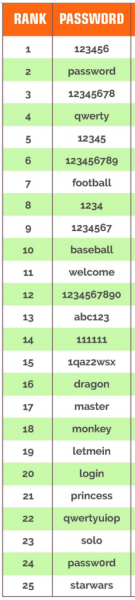 Here are the 25 most commonly used passwords for 2014. If your password is on this list, please understand that these passwords are among the first tried when automated password cracking software is used by a cyber-criminal. So if yours is here, change it now.
Here are the 25 most commonly used passwords for 2014. If your password is on this list, please understand that these passwords are among the first tried when automated password cracking software is used by a cyber-criminal. So if yours is here, change it now. Here’s a provocative statement: If you could just prevent your staff for clicking on links or opening attachments in phishing emails, 95% of your cybersecurity problems would be prevented.
Here’s a provocative statement: If you could just prevent your staff for clicking on links or opening attachments in phishing emails, 95% of your cybersecurity problems would be prevented.