 AV-Test rated Bitdefender Endpoint Security 5.3 the best anti-virus software for Windows client business users in its December 2015 test. I mention this because this is the product that we deploy here at CIT for our managed service customers. They rated a nearly perfect score. Here are the particulars:
AV-Test rated Bitdefender Endpoint Security 5.3 the best anti-virus software for Windows client business users in its December 2015 test. I mention this because this is the product that we deploy here at CIT for our managed service customers. They rated a nearly perfect score. Here are the particulars:
- 100% effective against zero-day malware out of 140 samples used
- 100% detection of 14,658 pervalent malware samples
- Bitdefender affected performance negliably, adding a ...
MAR

 Try to imagine how much bad stuff we could keep off our computers and networks if we could figure out a way to filter incoming traffic from the Dark Web. Well maybe we can.
Try to imagine how much bad stuff we could keep off our computers and networks if we could figure out a way to filter incoming traffic from the Dark Web. Well maybe we can. If you are in high school (or junior high) or college, attracted to technology, and looking for a career with a future, then you should give serious consideration to the field of Cybersecurity. A recent press release from
If you are in high school (or junior high) or college, attracted to technology, and looking for a career with a future, then you should give serious consideration to the field of Cybersecurity. A recent press release from  Last week we took an in depth look at social engineering, and looked a phone and email examples in depth.
Last week we took an in depth look at social engineering, and looked a phone and email examples in depth. Your phone rings. The caller identifies themselves as someone from a “tech support” company. Your computer has problems, he says, and he called to help you fix them. You agree to pay some sort of fee. You help them set up remote access to your computer. And now you have been hacked and helped them do it.
Your phone rings. The caller identifies themselves as someone from a “tech support” company. Your computer has problems, he says, and he called to help you fix them. You agree to pay some sort of fee. You help them set up remote access to your computer. And now you have been hacked and helped them do it. This should really be called “anti-social” engineering. A good definition is “social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter.”
This should really be called “anti-social” engineering. A good definition is “social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter.” Monday we looked at issues with the business class routers at Juniper Networks and Cisco Systems. Today we are going to look at an exploit affecting the Ubiquiti brand of cable modems.
Monday we looked at issues with the business class routers at Juniper Networks and Cisco Systems. Today we are going to look at an exploit affecting the Ubiquiti brand of cable modems. At the end of December last year Juniper Networks discovered that some malicious actors had added code to the firmware and software that run their routers, creating a back door that would allow attackers to access the router remotely, assume administrator privileges, and view and decrypt VPN traffic running through the routers. As the story unfolded, it turns out that Juniper was using a random number generator from NIST, and that the ...
At the end of December last year Juniper Networks discovered that some malicious actors had added code to the firmware and software that run their routers, creating a back door that would allow attackers to access the router remotely, assume administrator privileges, and view and decrypt VPN traffic running through the routers. As the story unfolded, it turns out that Juniper was using a random number generator from NIST, and that the ...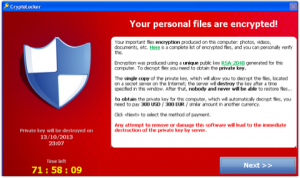 This is hot off the press. Yesterday
This is hot off the press. Yesterday