More fun from Pinterest.

FEB
 On Wednesday we took a broader look at the web browser. Today we are going take a deeper look at the Opera web browser, because they are doing some interesting things with privacy, security, and functionality.
On Wednesday we took a broader look at the web browser. Today we are going take a deeper look at the Opera web browser, because they are doing some interesting things with privacy, security, and functionality.
As I mentioned towards the end of Wednesday’s post, I am having concerns with my deep relationship with Google. Google for me has been like a really great girlfriend who anticipated my every need, and has now become ...
Continue Reading → What is a web browser? Can you name the ones you use? Here’s a hint: it is the most frequently used computer application. A computer application is a software program the performs a certain function. When you “surf the web,” access the Internet, shop online, keep in touch with Facebook, and for many people, read and send email, you are using a ...
What is a web browser? Can you name the ones you use? Here’s a hint: it is the most frequently used computer application. A computer application is a software program the performs a certain function. When you “surf the web,” access the Internet, shop online, keep in touch with Facebook, and for many people, read and send email, you are using a ...
One of these URLs will open your Gmail account. The other will take you to a replica phishing landing page to steal your Gmail password. Can you tell which is which?
![]()
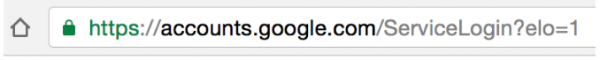
If you chose the first one as fake, and the second one as genuine, you ...
Continue Reading → Early on Jan. 9, about 12,000 MongoDB database servers were compromised. Later the number rose to 28,000 servers. As many as 46,000 servers are vulnerable to this attack.
Early on Jan. 9, about 12,000 MongoDB database servers were compromised. Later the number rose to 28,000 servers. As many as 46,000 servers are vulnerable to this attack.
A cyber-criminal using the alias “Harak1r1” exploited a weakness in the default installation of the popular database solution, MongoDB. He demanded a 0.2BTC ransom ($220) to return the data he exfiltrated from thousands of victim systems. Older installations of MongoDB that were deployed via cloud hosting services in an insecure default configuration ...
Continue Reading → We have complained in this blog about the plethora of Internet connected IoT devices that are being sold without anything approaching meaningful security to an unsuspecting public. A notable exploitation of IoT devices was behind the Mirai botnet, which shut down significant parts of the Internet for a couple of days.
We have complained in this blog about the plethora of Internet connected IoT devices that are being sold without anything approaching meaningful security to an unsuspecting public. A notable exploitation of IoT devices was behind the Mirai botnet, which shut down significant parts of the Internet for a couple of days.
But other disasters await, for instance, the easy access of web cams from the ...
Continue Reading →I have been working my way through a Cybrary course titled ” Incident Response and Advanced Forensics.” In it I came across the following slide, and what interested me was how it juxtaposed the Lockheed-Martin Cyber Kill Chain against a lower row of defensive tactics. The last option, hidden beneath the instructor’s image, is “Destroy.”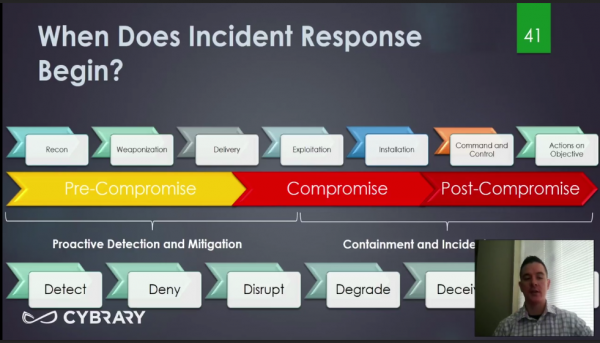
Where did this intriguing ...
Continue Reading → Is a good offense? If you or your company has been a victim of cyber-crime, I am sure you have had fantasies about back-hacking the perpetrators back to the stone age. Or having some sort of magic button phone app that would do the same thing.
Is a good offense? If you or your company has been a victim of cyber-crime, I am sure you have had fantasies about back-hacking the perpetrators back to the stone age. Or having some sort of magic button phone app that would do the same thing.
Currently, the bad guys are running the offense, 24/7/365. The good guys are limited to defense only. There ...
Continue Reading →