I have been working my way through a Cybrary course titled ” Incident Response and Advanced Forensics.” In it I came across the following slide, and what interested me was how it juxtaposed the Lockheed-Martin Cyber Kill Chain against a lower row of defensive tactics. The last option, hidden beneath the instructor’s image, is “Destroy.”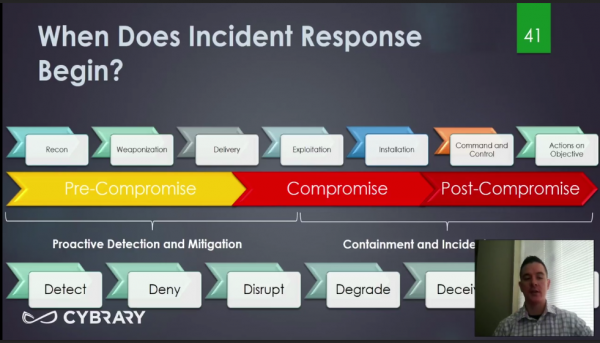
Where did this intriguing six step process come from? Upon further research, I found it included in an interesting document on the NIST website, called Operational Levels of Cyber Intellegence. At 16 pages (only 12 or so to read), I found it an interesting expansion on some of the ideas we discussed in Friday’s post.
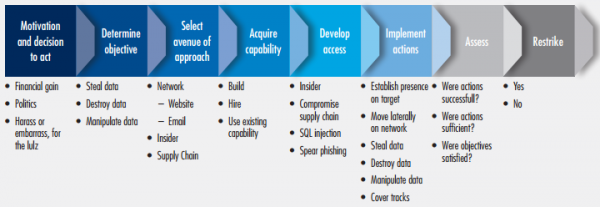
Here is an expansion of the Cyber Kill Chain from the attackers perspective. This gives more detail about the process that the attacker will be using to acquire and maintain access to your network.
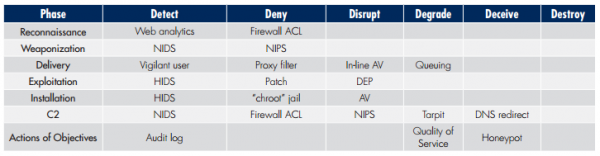
Here is the defenders process arrayed against the kill chain.
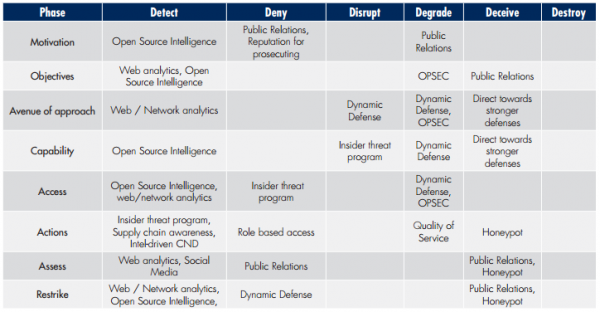
And here it is displayed against the expanded attack matrix.
If any of this is interesting to you, please click through to the source material. If you are looking to take your cybersecurity program from purely defensive to a more active and agressive defense , this will give you a good place to start.
More information:
- WyzGuys on the Cyber Kill Chain
- WyzGuys on Deterrence (from Friday)
- NIST Operational Levels of Cyber Intellegence
- Lockheed-Martin Cyber Kill Chain
JAN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com