Thanks to The Zebra for this infographic.
Continue Reading →JUL
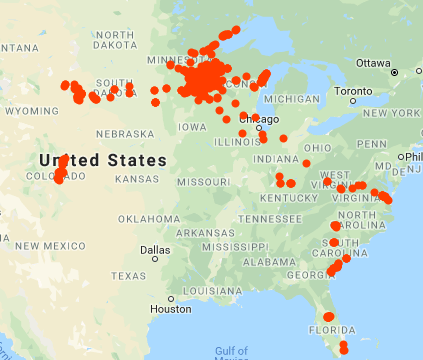 A lot of very specific location information is being collected about you, me, and every other smartphone user. The image at left shows everywhere I have been in the last four years, courtesy of Google location services. If you would like to find out what is being collected about you, and how to make it stop, the last article and this article ...
A lot of very specific location information is being collected about you, me, and every other smartphone user. The image at left shows everywhere I have been in the last four years, courtesy of Google location services. If you would like to find out what is being collected about you, and how to make it stop, the last article and this article ...
 A lot of very specific location information is being collected about you, me, and every other smartphone user. The image at left shows everywhere I have been in the last four years, courtesy of Google location services. If you would like to find out what is being collected about you, and how to make it stop, the next two articles will help. ...
A lot of very specific location information is being collected about you, me, and every other smartphone user. The image at left shows everywhere I have been in the last four years, courtesy of Google location services. If you would like to find out what is being collected about you, and how to make it stop, the next two articles will help. ...
 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.The US is alleged to have been quietly planting malware throughout Russia’s energy networks in response to years of Russian attacks on its own power grid.
My comment: Anybody who wonders why the bad guys are always attacking the US, well, it’s because we are doing it ...
Continue Reading → Identity theft is probably one of the most serious crimes that can happen to you. The bad news – identity theft in one fashion or another is likely to happen to all of us. In any given year, one in fifteen people will suffer identity theft. There are many ways that your personal information way end up in the hands ...
Identity theft is probably one of the most serious crimes that can happen to you. The bad news – identity theft in one fashion or another is likely to happen to all of us. In any given year, one in fifteen people will suffer identity theft. There are many ways that your personal information way end up in the hands ...
 The insider threat, the computer or network attack originating from inside our own network, is the hardest to defend. In our last post we took a look at the disgruntled employee and the embezzler. Today we will review insider-based sabotage and corporate espionage.
The insider threat, the computer or network attack originating from inside our own network, is the hardest to defend. In our last post we took a look at the disgruntled employee and the embezzler. Today we will review insider-based sabotage and corporate espionage.
Sabotage – Sometimes a disgruntled employee will take out their frustrations by orchestrating a little sabotage. Perhaps they ...
Continue Reading → Which is a bigger risk to your organization? A determined outsider trying to break into your network? Or an insider, an employee or coworker who is already on the network as a credentialed user? Obviously, it is the insider who represents the greatest threat.
Which is a bigger risk to your organization? A determined outsider trying to break into your network? Or an insider, an employee or coworker who is already on the network as a credentialed user? Obviously, it is the insider who represents the greatest threat.
In truth, all successful attacks become insider attacks. The determined outsider who finds a way into your network is ...
Continue Reading →I live in the People’s Republic of Minnesota. Wasn’t born here, but grew up here. Not sure why I stay here. More taxes here than anywhere else. Then there are the behavioral issues, such as Minnesota Nice. From BuzzFeed through Pinterest
Continue Reading →
 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.An very cool. detailed, and facinating look at how technology is changing and breaking the spy game from foreignpolicy.com. Worth the read.
The world of espionage is facing tremendous technological, political, legal, social, and commercial changes. The winners will be those who break the old rules of the ...
Continue Reading →