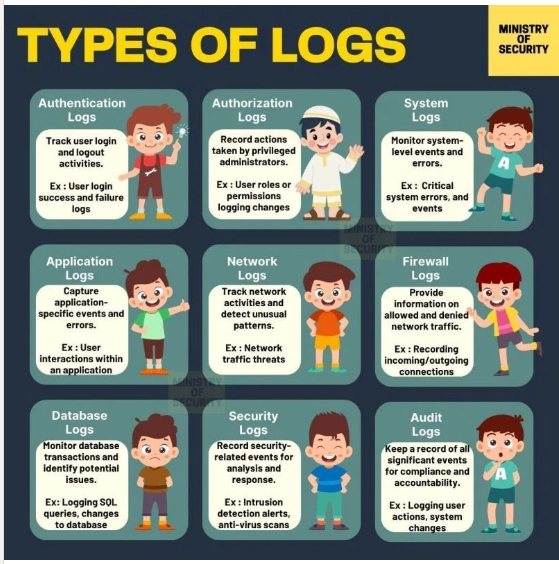
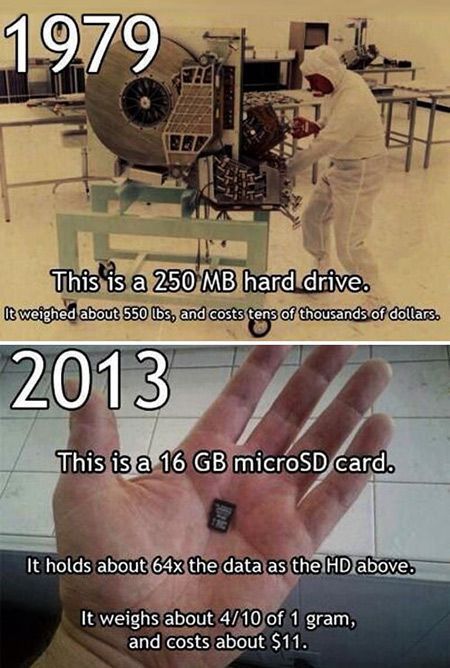
Most cybersecurity certifications focus heavily on the purpose and importance of log files. Log files are often aggregated and analyzed using tools and appliances such as SIEMs. Here is an infographic that I think is useful to help understand log files.
Continue Reading →
FEB